ESET researchers have recognized 5 campaigns concentrating on Android customers with trojanized apps. Most likely carried out by the Arid Viper APT group, these campaigns began in 2022 and three of them are nonetheless ongoing on the time of the publication of this blogpost. They deploy multistage Android spyware and adware, which we named AridSpy, that downloads first- and second-stage payloads from its C&C server to help it avoiding detection. The malware is distributed by devoted web sites impersonating varied messaging apps, a job alternative app, and a Palestinian Civil Registry app. Usually these are present functions that had been trojanized by the addition of AridSpy’s malicious code.
Key factors of the blogpost:
- ESET Analysis found three-stage Android malware, which we named AridSpy, being distributed through 5 devoted web sites.
- AridSpy’s code is in some circumstances bundled into functions that present professional performance.
- Whereas the primary stage of AridSpy has been documented beforehand, right here we additionally present a full evaluation of its beforehand unknown later phases.
- AridSpy is a remotely managed trojan that focuses on person information espionage.
- We detected six occurrences of AridSpy, in Palestine and Egypt.
- We attribute AridSpy with medium confidence to the Arid Viper APT group.
Arid Viper, also called APT-C-23, Desert Falcons, or Two-tailed Scorpion, is a cyberespionage group that has been lively since at least 2013. Recognized for concentrating on international locations within the Center East, the group has drawn consideration over time for its huge arsenal of malware for Android, iOS, and Windows platforms. We reported on the group and its then-newest spyware and adware in a earlier blogpost.
Overview
ESET Analysis recognized 5 Arid Viper campaigns concentrating on Android customers. These campaigns delivered malware through devoted web sites from which victims may obtain and manually set up an Android utility. Three apps offered on these web sites are professional apps trojanized with malicious code that we named AridSpy, whose objective is espionage. You may see the overview scheme in Determine 1.
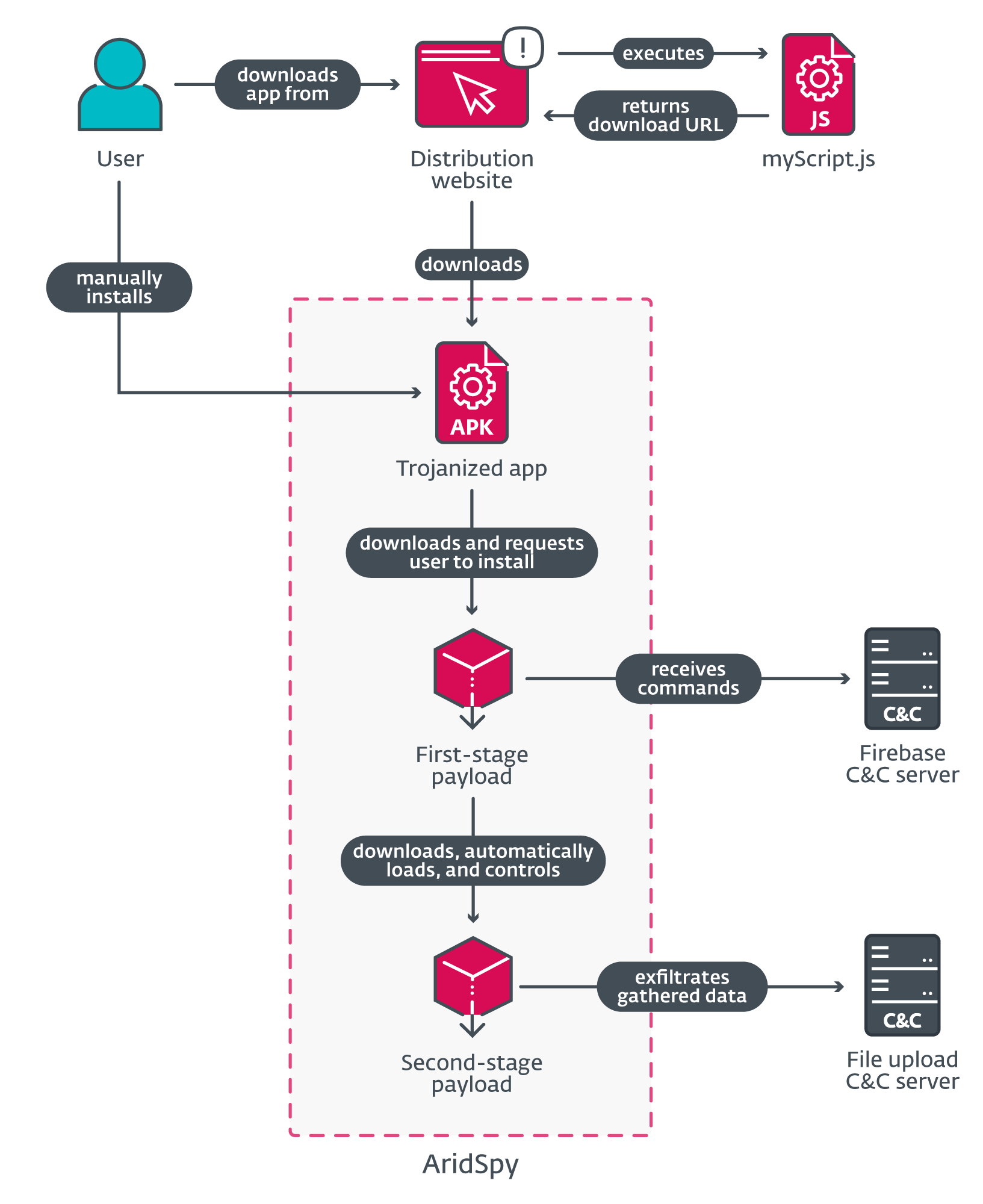
AridSpy was first analyzed by Zimperium in 2021; on the time, the malware solely consisted of a single stage, with all of the malicious code carried out within the trojanized utility.
The second incidence of AridSpy that ESET Analysis recognized was being utilized in 2022 (and later analyzed by 360 Beacon Labs in December 2022), the place the malware operators focused the FIFA World Cup in Qatar. Impersonating one of many many Kora functions, the marketing campaign deployed the Kora442 app bundled with AridSpy. As within the case of the pattern analyzed by Zimperium, the malware nonetheless solely had one stage presently.
In March 2023, 360 Beacon Labs analyzed one other Android marketing campaign operated by Arid Viper and located a connection between the Kora442 marketing campaign and the Arid Viper group, primarily based on use of the myScript.js file talked about in Determine 1. We discovered the identical connection within the campaigns mentioned on this blogpost (as defined within the Attribution part). It has confirmed to be a helpful indicator to determine further Arid Viper distribution web sites.
In August 2023 we logged a detection of AridSpy in our telemetry and investigated additional. We recognized targets in Palestine and Egypt. New in these campaigns, AridSpy was became a multistage trojan, with further payloads being downloaded from the C&C server by the preliminary, trojanized app.
On the time of this publication, three out of the 5 found campaigns are nonetheless lively; the campaigns used devoted web sites to distribute malicious apps impersonating NortirChat, LapizaChat, and ReblyChat, and the تطبيق المشغل (machine translation: Operator utility; we are going to discuss with this because the job alternative app) and السجل المدني الفلسطيني (machine translation: Palestinian Civil Registry) apps. We found the next distribution web sites through our telemetry, VirusTotal, and pivoting on the shared myScript.js script utilizing the FOFA network search engine (which is an alternative choice to Shodan and Censys):
- lapizachat[.]com
- reblychat[.]com
- nortirchats[.]com
- pariberychat[.]com (inactive)
- renatchat[.]com (inactive)
Parallel to our investigation, the FOFA analysis staff printed a blogpost that discusses discovering seven distribution web sites with the myScript.js JavaScript file chargeable for retrieving the obtain paths for Arid Viper payloads. 4 of those web sites distributed varied variations of AridSpy. The next two had been beforehand unknown to us:
- clemochat[.]com
- voevanil[.]com
On this blogpost, we concentrate on AridSpy payloads that we may get hold of from all of the confirmed lively distribution web sites listed above.
Be aware that these malicious apps have by no means been supplied by Google Play and are downloaded from third-party websites. To put in these apps, the potential sufferer is requested to allow the non-default Android possibility to put in apps from unknown sources.
Victimology
Altogether we detected six occurrences of AridSpy in our telemetry, from Palestine and Egypt. The vast majority of the spyware and adware situations registered in Palestine had been for the malicious Palestinian Civil Registry app, with one different detection not being a part of any marketing campaign talked about on this blogpost. We then discovered the identical first-stage payload however with a special package deal identify in Egypt. There was additionally one other first-stage payload detected in Egypt, one which makes use of the identical C&C servers because the samples within the LapizaChat and job alternative campaigns.
Attribution
We attribute AridSpy to Arid Viper with medium confidence, primarily based on these indicators:
- AridSpy focused organizations in Palestine and Egypt, which inserts a subset of Arid Viper’s typical concentrating on.
- A number of AridSpy distribution web sites use a novel, malicious JavaScript file named myScript.js, which has been beforehand linked to Arid Viper by 360 Beacon Labs and FOFA.
myScript.js was first found and linked to Arid Viper in 360 Beacon Labs’ March 30th, 2023 analysis of a special Android marketing campaign operated by Arid Viper. The (unnamed) malicious Android code utilized in that marketing campaign was previously attributed to the Arid Viper group. myScript.js was discovered on one of many distribution web sites used within the marketing campaign. The aim of this JavaScript code was to obtain a malicious Android app hosted on the distribution server.
Determine 2 exhibits the a part of the code that registers the handler for clicks on the web site’s Obtain button, and Determine 3 shows JavaScript code that generates file paths to obtain the malicious app.
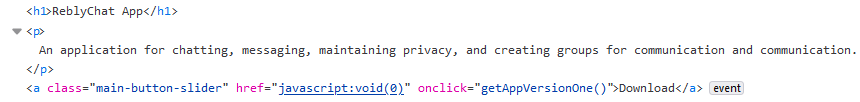
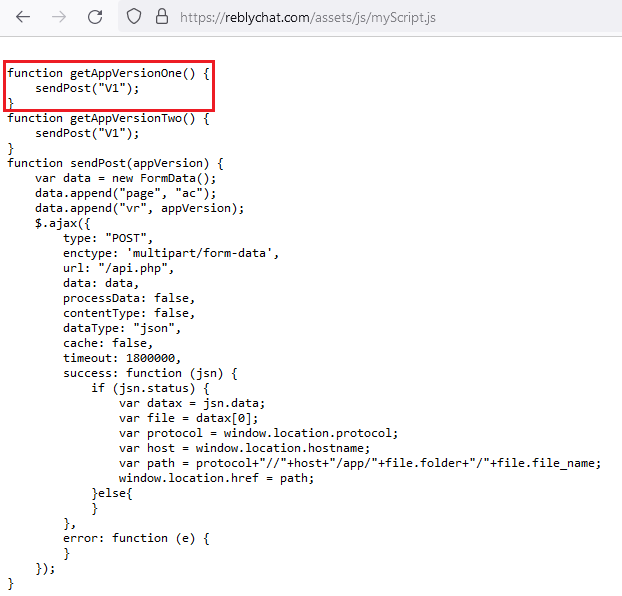
As identified by 360 Beacon Labs, this identical JavaScript code was additionally used within the marketing campaign that focused the FIFA World Cup in Qatar with an earlier model of AridSpy, which we reported in 2022. In each campaigns, the distribution web sites used this particular myScript.js script to retrieve a malicious app from a server, though the ultimate payload was completely different.
Lastly, we discovered a really comparable piece of JavaScript on the distribution web sites for the campaigns mentioned on this blogpost, distributing NortirChat, LapizaChat, and ReblyChat. Throughout our investigation, this linkage was independently confirmed by the analysis staff of the FOFA search engine, who discovered seven of the identical distribution web sites that contained the myScript.js chargeable for downloading Android AridSpy, and attributed this malware to Arid Viper.
We’ve got not been capable of hyperlink the JavaScript code utilized in these campaigns to any professional or open-source venture, which leads us to consider that this script is most certainly particular to numerous Arid Viper campaigns distributing Android malware.
It’s attainable that Arid Viper reused this distribution methodology, however switched to a brand new software, AridSpy, for its new campaigns, because the (unnamed) malware household the group used earlier than was disclosed and analyzed by varied researchers and safety corporations.
Apparently, we additionally found a special model of myScript.js on the AridSpy distribution website, masquerading as a Palestinian Civil Registry app. On this case, the script had the identical objective however not the identical JavaScript code: as a substitute of downloading AridSpy, this script simply returned a hardcoded hyperlink to AridSpy.
This model of the script relies on a script available online, opposite to the sooner variations that seem to make use of a custom-developed myScript.js file. When the sooner variations of myScript.js had been disclosed and attributed to Arid Viper, the risk actors most certainly modified its code to keep away from their new code being related to the group.
Technical evaluation
Preliminary entry
The distribution mechanism may be very comparable for all campaigns talked about on this part. To be able to acquire preliminary entry to the gadget, the risk actors attempt to persuade their potential sufferer to put in a faux, however purposeful, app. As soon as the goal clicks the positioning’s Obtain button, myScript.js, hosted on the identical server, is executed to generate the right obtain file path for the malicious AridSpy. This script makes an AJAX request to api.php situated on the identical server and returns a particular file listing and identify.
Trojanized messaging functions
Beginning chronologically, we are going to first take a look at the marketing campaign posing as LapizaChat, a malicious Android utility that was obtainable for obtain from the devoted lapizachat[.]com web site. This web site was registered on January 16th, 2022 and is not lively. Its interface could be seen in Determine 4.
In an open listing on the server, there was not one, however truly three LapizaChat Android apps, saved in several directories. One of many apps was a replica of the professional StealthChat: Private Messaging app and had no malicious performance. It contained the identical professional messaging code as StealthChat, however with completely different utility icon, identify, and package deal identify. This app has been obtainable on the distribution web site since January 18th, 2022.
The opposite two apps had been trojanized variations of StealthChat: Personal Messaging bundled with AridSpy’s malicious code. Primarily based on the final modification date, they had been obtainable on the server since July 5th, 2023 and September 18th, 2023 respectively, primarily based on the final modification date. The 2 malicious apps are similar to one another; the latter pattern incorporates the identical malicious code, with solely minor, insignificant adjustments. It was this model that the sufferer would obtain from the web site after clicking the Obtain Now button. Filenames, final modification dates, and hashes are listed in Desk 1.
Desk 1. Samples obtainable on lapizachat[.]com web site
|
Filename |
Final modified |
SHA-1 |
Description |
|
LapizaChat.apk |
2022‑01‑18 |
D99D9689A7C893AFCE84 |
The professional StealthChat: Private Messaging utility, model 1.8.42 (6008042). |
|
LapizaChat_old.apk |
2023‑07‑05 |
3485A0A51C6DAE251CDA |
StealthChat trojanized with AridSpy, distributed below the identify LapizaChat. |
|
LapizaChat.apk |
2023‑09‑18 |
F49B00896C99EA030DCC |
We recognized two different campaigns that began distributing AridSpy after LapizaChat, this time posing as messaging apps named NortirChat and ReblyChat. They had been distributed (after clicking on the Obtain button) through the web sites nortirchats[.]com, registered on September 21st, 2022, and reblychat[.]com, registered on April 30th, 2023; see Determine 5.

Much like the earlier case, we had been capable of retrieve further samples from open directories, together with each the clear and trojanized variations of the messaging functions. NortirChat relies on the professional Session messaging app, whereas ReblyChat relies on the professional Voxer Walkie Talkie Messenger. In each circumstances, the trojanized functions have the identical code however the malware builders modified the appliance icon, identify, and package deal identify. Desk 2 and Desk 3 checklist particulars of the functions retrieved from these servers.
Desk 2. Samples obtainable on nortirchats[.]com web site
|
Filename |
Final modified |
SHA-1 |
Description |
|
NortirChat_old.apk |
2022‑09‑28 |
13A89D28535FC1D53794 |
The professional Session messaging app, model 1.16.5 (3331). |
|
NortirChat.apk |
2023‑03‑19 |
1878F674F59E81E86986 |
|
|
NortirChat_old.apk |
2023‑06‑14 |
2158D88BCE6368FAC3FC |
Session app trojanized with AridSpy, distributed below the identify NortirChat. |
|
NortirChat.apk |
2023‑09‑11 |
DB6B6326B772257FDDCB |
Desk 3. Samples obtainable on reblychat[.]com web site
|
Filename |
Final modified |
SHA-1 |
Description |
|
reblychat.apk |
2023‑06‑08 |
FFDD0E387EB3FEF7CBD2 |
The professional Voxer Walkie Talkie Messenger utility, model 4.0.2.22408 (3669119). |
|
reblychat-old.apk |
2023‑06‑08 |
A64D73C43B41F9A5B938 |
The Voxer Walkie Talkie Messenger app trojanized with AridSpy, distributed below the identify ReblyChat. |
|
reblychat.apk |
2023‑06‑11 |
797073511A15EB85C1E9 |
Masquerading as a Palestinian Civil Registry utility
Shifting on from trojanizing chat functions in the interim, the operators then launched a marketing campaign distributing an app purporting to be from the Palestinian Civil Registry (السجل المدني الفلسطيني). The malicious app claims to supply normal details about the residents of Palestine, akin to identify, place of residence, date of beginning, ID quantity, and different info. This marketing campaign offers a malicious Android app obtainable for obtain from palcivilreg[.]com, registered on Could 30th, 2023; see Determine 6.
![Figure 6. palcivilreg[.]com website](https://web-assets.esetstatic.com/wls/2024/6-2024/arid-viper/figure6.png)
Machine translation of the web site from Determine 6: “Palestinian Civil Registry. To seek out out details about any particular person or seek for any particular person’s id quantity or date of beginning, obtain the appliance to look the Palestinian civil registry.”
This web site is marketed through a devoted Facebook page – see Determine 7 – that was created on July 25th, 2023 and hyperlinks on to palcivilreg[.]com. We’ve got reported this web page to Fb.
![Figure 7. Facebook page promoting the palcivilreg[.]com website for every Palestinian to identify personal data Figure 7. Facebook page promoting the palcivilreg[.]com website for every Palestinian to identify personal data](https://web-assets.esetstatic.com/wls/2024/6-2024/arid-viper/figure7.png)
Machine translation of the quilt photograph seen in Determine 7: “Palestinian Civil Registry. Seek for any particular person’s identify and acquire his full information. Get date of beginning and age of any particular person. Ease of looking and getting into the appliance.”
Choosing the تحميل (Obtain, in Arabic; see Determine 6) button executes myScript.js, initiating obtain from a hardcoded URL; see Determine 8. This occasion of myScript.js code is barely modified, in comparison with beforehand talked about campaigns, however achieves the identical outcomes – retrieving a file from a malicious hyperlink. This model of the script could be discovered in lots of tutorials obtainable on-line; one among its first occurrences appears to be from February 2019.
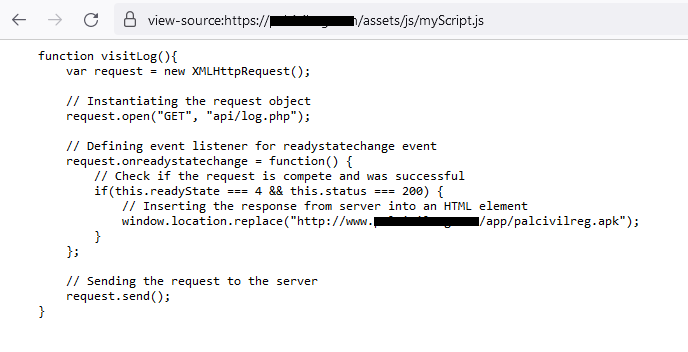
The Palestinian Civil Registry app is impressed by an app on Google Play that has been obtainable for obtain since March 2020 and offers the identical performance as claimed on the palcivilreg[.]com website. The app on Google Play is linked to the web site zezsoft.wuaze[.]com, which permits downloading iOS and Android apps. On the time of this analysis, the iOS utility was not obtainable, and the Android app hyperlink refers back to the file-sharing storage website MediaFire, to not Google Play. This app was not obtainable from MediaFire, so we aren’t capable of affirm whether or not that model was professional.
Primarily based on our investigation, the malicious app obtainable on palcivilreg[.]com is just not a trojanized model of the app on Google Play; nonetheless, it makes use of that app’s professional server to retrieve info. Which means that Arid Viper was impressed by that app’s performance however created its personal shopper layer that communicates with the professional server. Almost definitely, Arid Viper reverse engineered the professional Android app from Google Play and used its server for retrieving victims’ information.
Masquerading as a job portal utility
The final marketing campaign we recognized distributes AridSpy as an app named تطبيق المشغل (machine translation: Operator utility; we discuss with this because the job alternative app), obtainable for obtain from almoshell[.]web site, registered on August 19th, 2023. This web site claims to supply a job to anybody who applies by the Android app. On this case, the malicious app is just not a trojanized model of any professional app. When supposedly making use of for a job, AridSpy makes requests to almoshell[.]web site for registered customers. This service runs on a malware distribution web site, so it’s troublesome to determine whether or not any related work provides are returned to the app’s person or not. The web site is proven in Determine 9.
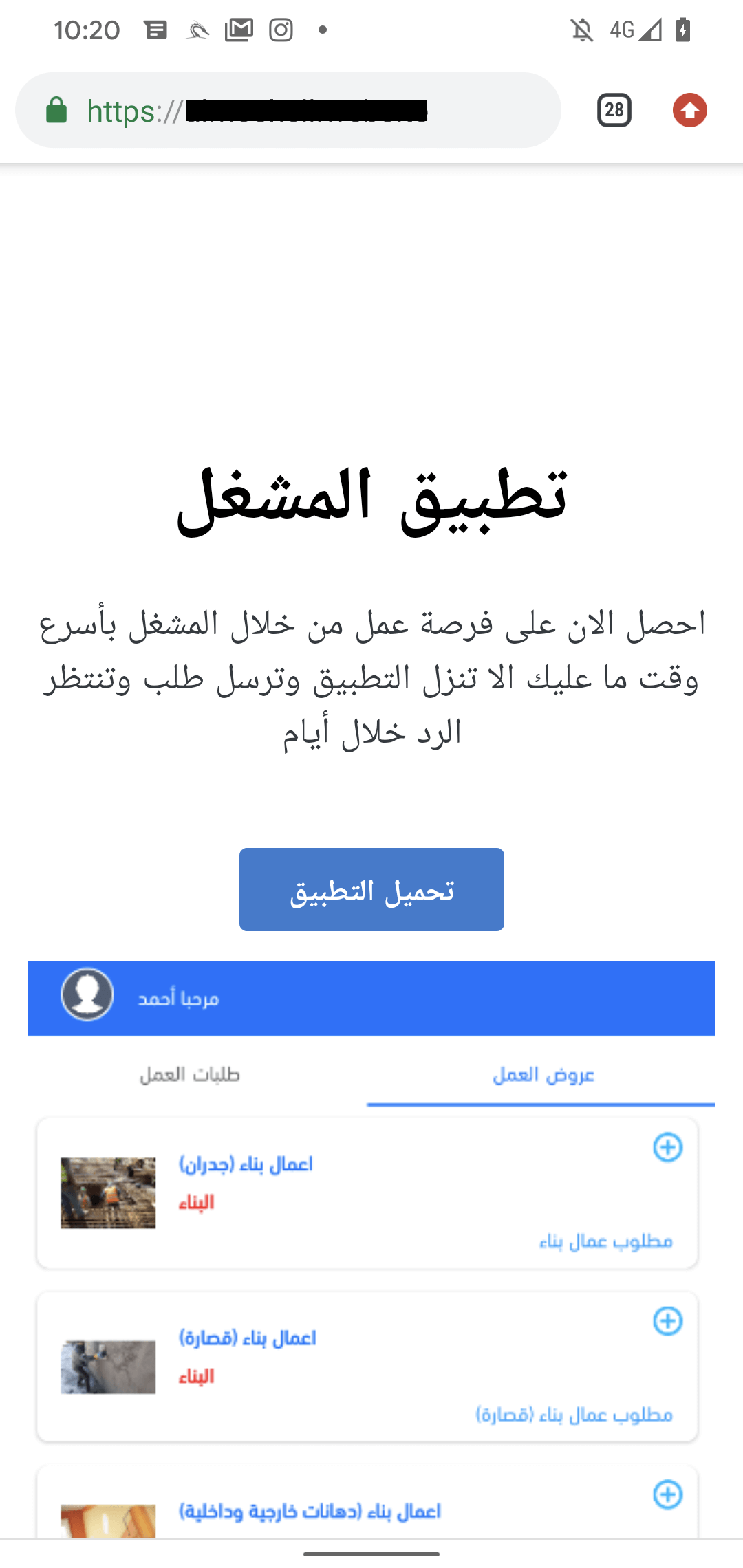
The job alternative app has been obtainable for obtain from this distribution website since August 20th, 2023; see Determine 10.
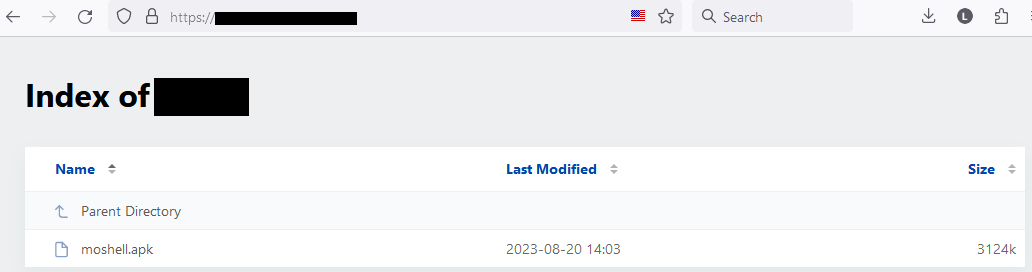
Toolset
All analyzed Android apps from these campaigns include comparable malicious code, and obtain first- and second-stage payloads; our evaluation focuses on the NortirChat and LapizaChat campaigns, the place we had been capable of get hold of the ultimate payloads.
Trojanized utility
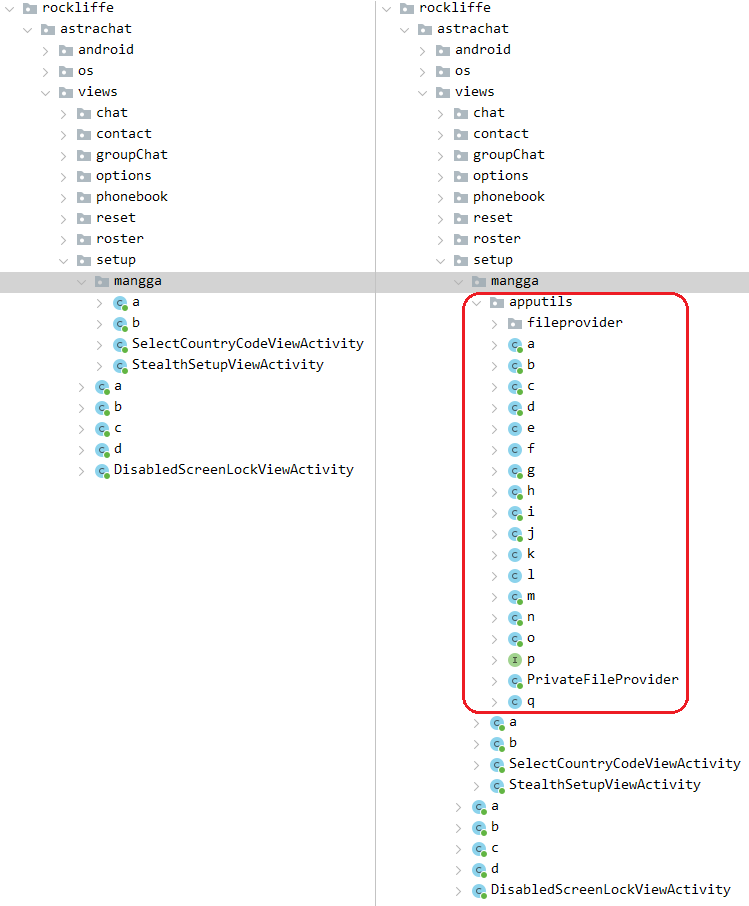
The campaigns largely deploy professional apps which were trojanized. Within the analyzed LapizaChat and NortirChat circumstances, malicious performance chargeable for downloading a payload is carried out within the apputils subpackage inserted into the professional messaging apps, as could be seen in Determine 11.
After the preliminary begin of the app, the malware seems to be for put in safety software program primarily based on a hardcoded checklist of dozens of safety functions, and reviews the outcomes to the C&C server. The whole checklist of those apps, together with their package deal names, is in Desk 4.
Desk 4. Listing of safety apps within the order that they seem within the code
|
App identify |
Bundle identify |
|
Bitdefender Cellular Safety |
com.bitdefender.safety |
|
Avast Antivirus & Safety |
com.avast.android.mobilesecurity |
|
McAfee Safety: Antivirus VPN |
com.wsandroid.suite |
|
Avira Safety Antivirus & VPN |
com.avira.android |
|
Malwarebytes Cellular Safety |
org.malwarebytes.antimalware |
|
Kaspersky: VPN & Antivirus |
com.kms.free |
|
ESET Cellular Safety Antivirus |
com.eset.ems2.gp |
|
Sophos Intercept X for Cellular |
com.sophos.smsec |
|
Dr.Internet Safety House |
com.drweb.professional |
|
Cellular Safety & Antivirus |
com.trendmicro.tmmspersonal |
|
Fast Heal Complete Safety |
com.quickheal.platform.advance.blue.market |
|
Antivirus and Cellular Safety |
com.quickheal.platform |
|
Safety Antivirus Max Cleaner |
com.maxdevlab.cleaner.safety |
|
AVG AntiVirus & Safety |
com.antivirus |
|
APUS Safety:Antivirus Grasp |
com.guardian.safety.pri |
|
Norton360 Cellular Virus Scanner |
com.symantec.mobilesecurity |
|
360 Safety |
com.qihoo.safety |
|
Lookout Life – Cellular Safety |
com.lookout |
|
dfndr safety: antivirus |
com.psafe.msuite |
|
Virus Cleaner, Antivirus Clear |
telephone.antivirus.virus.cleaner.junk.clear.velocity. |
|
Antivirus & Virus Cleaner Lock |
com.antivirus.mobilesecurity.viruscleaner.applock |
|
GO Safety-AntiVirus, AppLock, Booster |
com.jb.safety |
|
Zimperium MTD |
com.zimperium.zips |
|
Intune Firm Portal |
com.microsoft.windowsintune.companyportal |
|
Lively Protect Enterprise |
com.higher.lively.protect.enterprise |
|
Concord Cellular Shield |
com.lacoon.safety.fox |
|
Lookout for Work |
com.lookout.enterprise |
|
Trellix Cellular Safety |
com.mcafee.mvision |
|
Microsoft Defender: Antivirus |
com.microsoft.scmx |
|
Sophos Cellular Management |
com.sophos.mobilecontrol.shopper.android |
|
Jamf Belief |
com.wandera.android |
|
SEP Cellular |
com.skycure.skycure |
|
Pradeo Safety |
web.pradeo.service |
If safety software program on the checklist is put in on the gadget, the malware will ship this info to the C&C server. If the server returns the worth 0, then the first-stage payload is not going to be downloaded. If the server returns the worth 1, then AridSpy proceeds and downloads the first-stage payload. In all circumstances that we noticed, when a safety app was put in on the gadget, the server returned the worth 0 and payloads weren’t downloaded.
AridSpy makes use of trivial string obfuscation, the place every string is asserted by changing a personality array right into a string. This methodology was utilized in each pattern and even within the first printed evaluation by Zimperium. That very same obfuscation can be utilized within the first- and second-stage payloads. Determine 12 exhibits an instance.
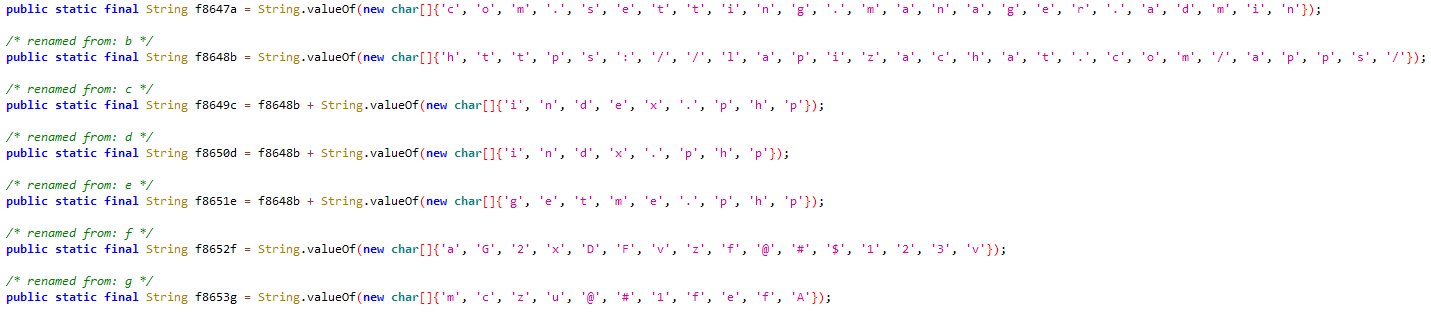
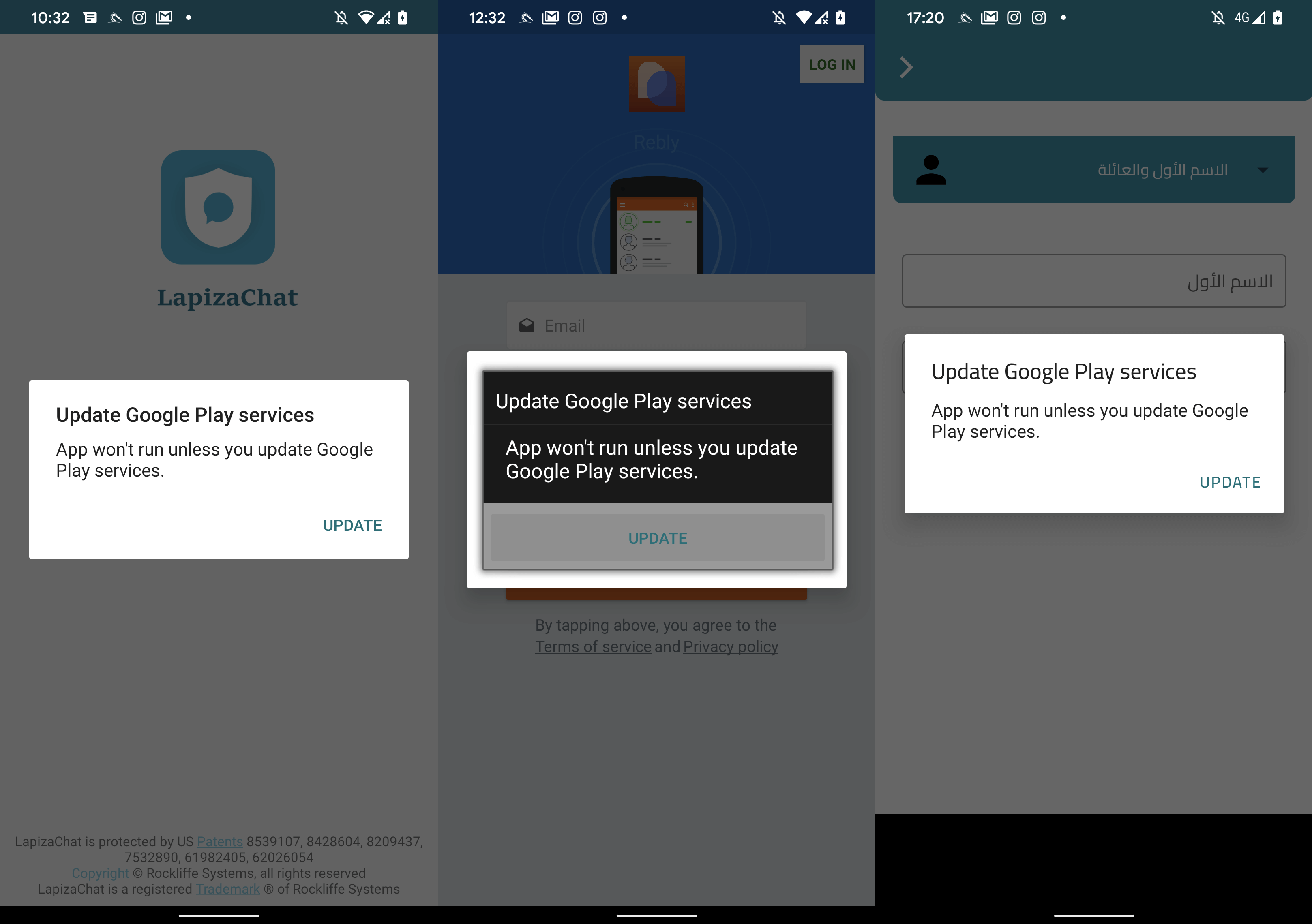
If safety software program is just not put in, AridSpy downloads the AES-encrypted first-stage payload from its C&C server. This payload is then decrypted utilizing a hardcoded key, and the potential sufferer is requested to put in it manually. The primary-stage payload impersonates an replace of Google Play providers, as displayed in Determine 13.
First-stage payload
Throughout set up of the malicious replace, the first-stage payload shows app names akin to Play Supervisor or Service Google. This payload works individually, with out the need of getting the trojanized app put in on the identical gadget. Which means that if the sufferer uninstalls the preliminary trojanized app, for instance LapizaChat, AridSpy is not going to be in any means affected.
Performance-wise, the first-stage payload is just like the trojanized utility. It’s chargeable for downloading the second-stage payload, which is then dynamically loaded and executed. The primary-stage payload downloads an AES-encrypted second-stage payload from a hardcoded URL and controls its additional execution.
Second-stage payload
The second-stage payload is a Dalvik executable (dex); primarily based on our observations, it all the time has the identify prefLog.dex. The malicious performance is carried out on this stage; nonetheless, it’s operated by the first-stage payload, which masses it at any time when mandatory.
AridSpy makes use of a Firebase C&C area for receiving instructions, and a special, hardcoded C&C area, for information exfiltration. We reported the Firebase servers to Google, because it offers the service.
When payloads are downloaded and executed, AridSpy units listeners to observe when the gadget display screen is on and off. If the sufferer locks or unlocks the telephone, AridSpy will take an image utilizing the entrance digital camera and ship it to the exfiltration C&C server. Photos are taken solely whether it is greater than 40 minutes because the final image was taken and the battery degree is above 15%. By default, these photos are taken utilizing the entrance digital camera; nonetheless, this may be modified by receiving a command from the Firebase C&C server to make use of the rear digital camera. Pictures are archived within the information.zip file on inside storage and uploaded to the exfiltration C&C server.
AridSpy has a function supposed to keep away from community detection – particularly C&C communication. It could possibly deactivate itself, as AridSpy states within the code, by altering the exfiltration C&C server used for information add to a dummy hardcoded androidd[.]com area (a at the moment registered typosquat). This motion happens primarily based on a command obtained from the Firebase C&C server. The dummy area would most likely look extra professional, is just not flagged as malicious, and won’t set off community detection techniques.
Knowledge exfiltration is initiated both by receiving a command from the Firebase C&C server or when a particularly outlined occasion is triggered. These occasions are outlined in AndroidManifext.xml and are prompted when actions happen, akin to: web connectivity adjustments, the app is put in or uninstalled, a telephone name is made or obtained, an SMS message is distributed or obtained, a battery charger is related or disconnected, or the gadget reboots.
If any of those occasions happens, AridSpy begins to collect varied sufferer information and uploads it to the exfiltration C&C server. It could possibly gather:
- gadget location,
- contact checklist,
- name logs,
- textual content messages,
- thumbnails of images,
- thumbnails of recorded movies,
- recorded telephone calls,
- recorded surrounding audio,
- malware-taken images,
- file construction of exterior storage,
- six WhatsApp databases (wa.db-wal, wa.db-shm, wa.db, msgstore.db-wal, msgstore.db-shm, msgstore.db) that include exchanged messages and person contacts, if the gadget is rooted,
- bookmarks and search historical past from the default browser and Chrome, Samsung Browser, and Firefox apps if put in,
- information within the clipboard,
- recordsdata from exterior storage with file measurement smaller than 30 MB and extensions .pdf, .doc, .docx, .xls, .xlsx, .ppt, .pptx, and .opus,
- thumbnails from the Samsung Gallery app saved within the /storage/emulated/0/Android/information/com.sec.android.gallery3d/cache/ listing,
- all obtained notifications,
- Fb Messenger and WhatsApp communication, and
- logs of all textual content seen by misusing Accessibility providers.
In addition to ready for occasions to happen, the Arid Viper operator can extract particular info and add it instantly to the exfiltration C&C server by sending instructions to the compromised gadget. AridSpy can obtain instructions from its Firebase C&C server to acquire information or to regulate the malware. Operators can exfiltrate:
- gadget location,
- contact checklist,
- textual content messages,
- name logs,
- thumbnails of images,
- thumbnails of recorded movies,
- a particular picture from exterior storage primarily based on an ID obtained from the Firebase C&C server,
- a particular video from exterior storage primarily based on an ID obtained from the Firebase C&C server,
- recorded audio,
- pictures taken on demand,
- a particular file by file path obtained from the C&C, and
- gadget information akin to whether or not Fb Messenger and WhatsApp apps are put in, gadget storage, battery proportion, web connection, Wi-Fi connection information, display screen on or off standing, and the time zone.
By receiving management instructions, it could:
- deactivate communication by changing the exfiltration C&C area with the dummy worth androidd[.]com,
- activate communication by changing the dummy androidd[.]com C&C area with one other area identify,
- permit information add when on a cell information plan, and
- change the exfiltration C&C server for information add.
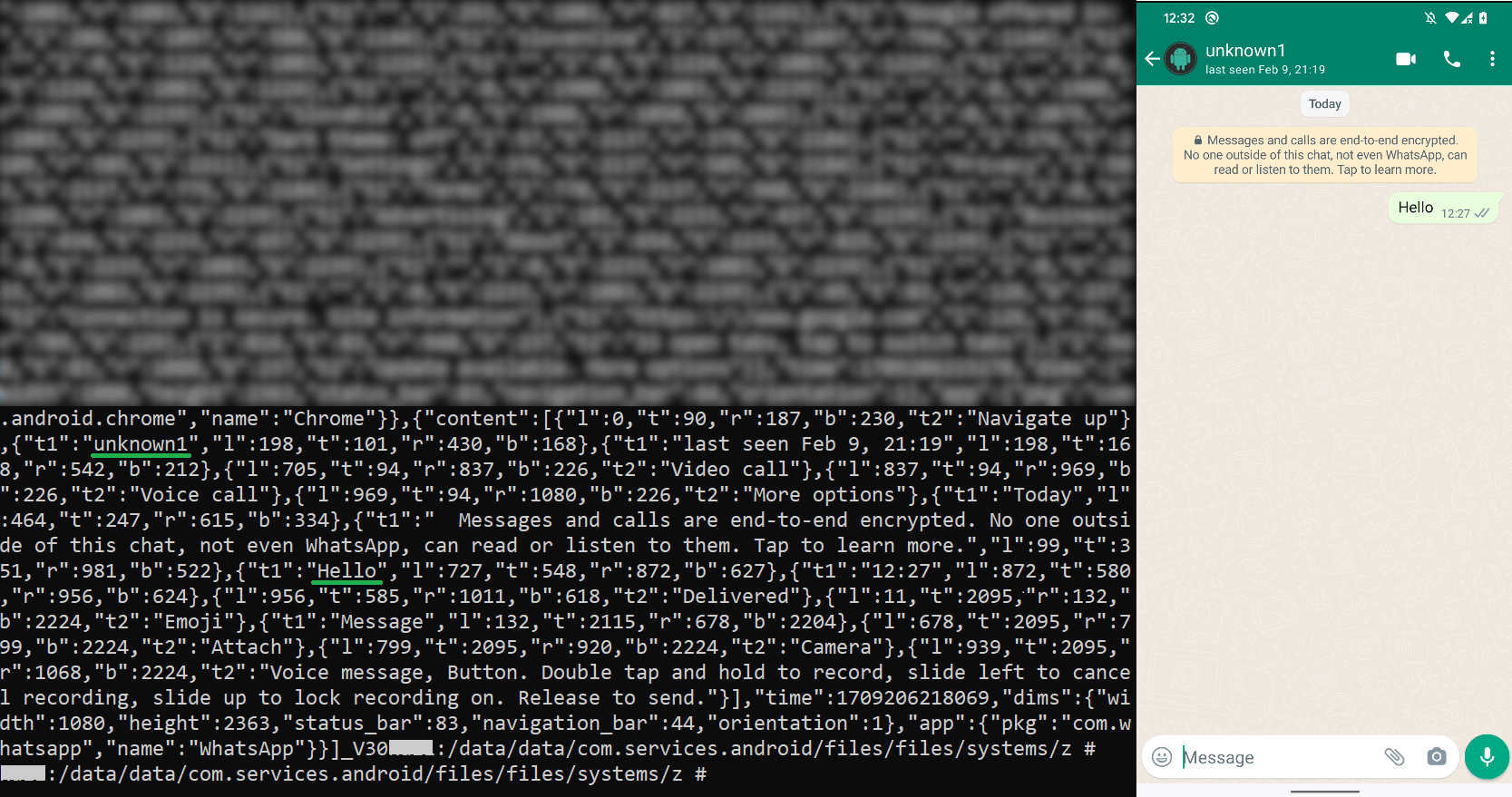
AridSpy can eavesdrop on person exercise by keylogging all textual content seen and editable in any utility. On prime of that, it particularly focuses on Fb Messenger and WhatsApp communications, that are saved and exfiltrated individually. To perform this activity, it misuses built-in accessibility providers to file all textual content seen and uploads it to the exfiltration C&C server. Examples of saved WhatsApp communications could be seen in Determine 14.
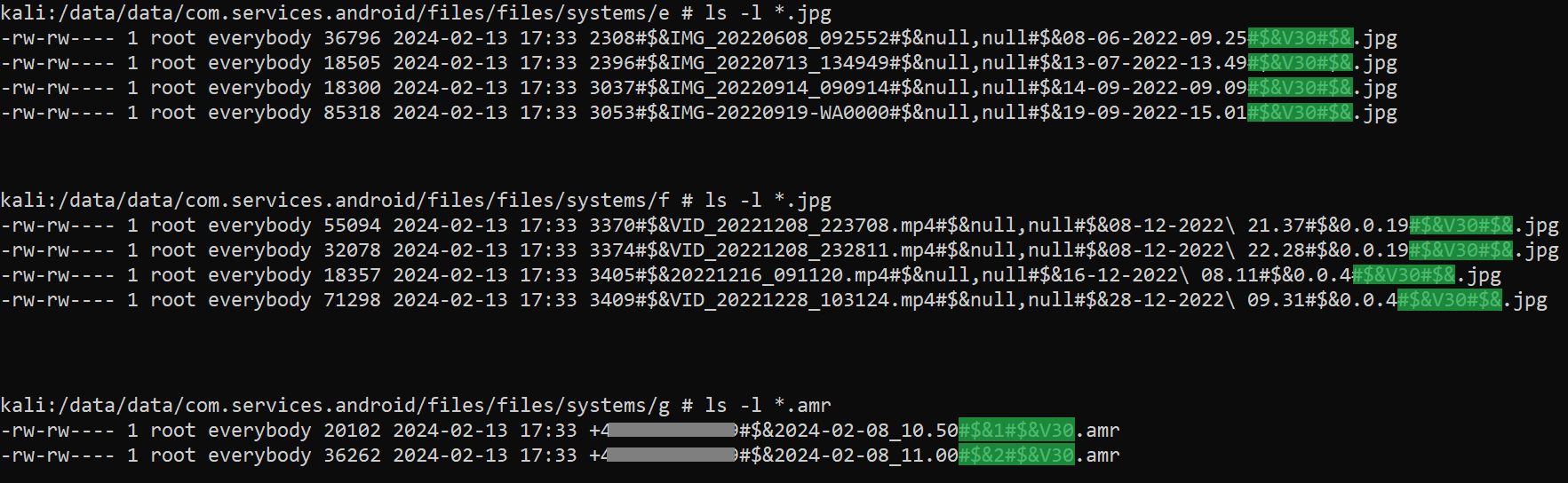
Earlier than collected information is uploaded to the exfiltration C&C server, it’s saved on inside storage, in /information/information/<package_name>/recordsdata/recordsdata/techniques/, that belongs to AridSpy. The obtained contact checklist, SMS, name logs, location, captured keys, file constructions, and different textual content info are saved in plain textual content as JSON recordsdata. All exfiltrated information is saved utilizing particular filenames which may include file IDs, filenames, time stamps, location, telephone quantity, and AridSpy model. These values are divided by the delimiter #$&, as could be seen in Determine 15.
All these recordsdata from any explicit subdirectory are then zipped into information.zip and encrypted utilizing {custom} encryption. Every of the encrypted recordsdata makes use of a randomly generated filename with the _Father.zip suffix. This string is hardcoded and appended to each file. The recordsdata are then uploaded to the exfiltration C&C server and faraway from the gadget.
Whereas going by the decompiled AridSpy code, we recognized a model quantity, which is used as a part of the filename when exfiltrating sufferer information (#$&V30#$&), additionally seen in Determine 15 (highlighted is the model quantity). The AridSpy model has been altering throughout the campaigns and was included even with its first variant disclosed in 2021. For among the AridSpy samples, the model quantity is current within the trojanized app and in addition within the second-stage payload. This model could be completely different, because the downloaded payload could be up to date. In Desk 5, you may see the package deal names and their variations. Some trojanized apps contained the model quantity solely of their payloads, not within the physique of the executable.
Desk 5. Malware variations present in samples
|
App identify |
Bundle identify |
SHA-1 |
Model |
|
System Replace |
com.replace.system.vital |
52A508FEF60082E1E4EC |
22 |
|
[without app name] |
com.climate.providers.supervisor |
A934FB482F61D85DDA5E |
26 |
|
[without app name] |
com.studio.supervisor.app |
5F0213BA62B84221C962 |
26 |
|
Kora442 |
com.app.projectappkora |
60B1DA6905857073C4C4 |
27 |
|
تطبيق المشغل |
com.app.workapp |
568E62ABC0948691D672 |
29 |
|
NortirChat |
cx.ring |
DB6B6326B772257FDDCB |
30 |
|
prefLog.dex |
com.providers.android.handler |
16C8725362D1EBC8443C |
30 |
|
prefLog.dex |
com.setting.supervisor.admin.handler |
E71F1484B1E3ACB4C8E8 |
31 |
The Model column of the desk means that the malware is recurrently maintained.
It’s price mentioning that the trojanized malicious apps used for the Palestinian Civil Registry and job alternative campaigns have carried out malicious performance that’s then additionally offered within the second-stage payload. It appears very uncommon to obtain a payload if the identical performance is already included. The duplicated malicious performance doesn’t appear to be an supposed habits, as it isn’t carried out in samples for different campaigns; relatively, it could be code left over from a time earlier than the malware was up to date to supply two further phases. Even so, these two trojanized apps can obtain instructions and spy on victims without having further payloads. Naturally, the second-stage payload carries the most recent updates and malicious code adjustments, which could be pushed to different ongoing campaigns.
Conclusion
5 campaigns, most certainly operated by the Arid Viper APT group, distribute Android spyware and adware, which we have named AridSpy, through devoted web sites, with AridSpy’s malicious code implanted into varied trojanized apps. This malware household has two further phases which can be downloaded from a C&C server. The aim of the second-stage payload is espionage through sufferer information exfiltration. AridSpy additionally has a hardcoded inside model quantity that differs in these 5 campaigns and from different samples disclosed earlier than. This info means that AridSpy is maintained and would possibly obtain updates or performance adjustments.
For any inquiries about our analysis printed on WeLiveSecurity, please contact us at threatintel@eset.comESET Analysis provides non-public APT intelligence reviews and information feeds. For any inquiries about this service, go to the ESET Threat Intelligence web page.
IoCs
A complete checklist of Indicators of Compromise (IoCs) and samples could be present in our GitHub repository.
Information
|
SHA-1 |
Filename |
Detection |
Description |
|
797073511A15EB85C1E9 |
com.rebelvox.rebly.apk |
Android/Spy.AridSpy.A |
AridSpy trojanized utility. |
|
5F0213BA62B84221C962 |
com.studio.supervisor.app.apk |
Android/Spy.AridSpy.A |
The primary stage of AridSpy. |
|
A934FB482F61D85DDA5E |
com.climate.providers. |
Android/Spy.AridSpy.A |
The primary stage of AridSpy. |
|
F49B00896C99EA030DCC |
com.chat.lapiza.apk |
Android/Spy.AridSpy.A |
AridSpy trojanized utility. |
|
3485A0A51C6DAE251CDA |
com.chat.lapiza.apk |
Android/Spy.AridSpy.A |
AridSpy trojanized utility. |
|
568E62ABC0948691D672 |
com.app.workapp.apk |
Android/Spy.AridSpy.A |
AridSpy trojanized utility. |
|
DB6B6326B772257FDDCB |
cx.ring.apk |
Android/Spy.AridSpy.A |
AridSpy trojanized utility. |
|
2158D88BCE6368FAC3FC |
cx.ring.apk |
Android/Spy.AridSpy.A |
AridSpy trojanized utility. |
|
B806B89B8C44F4674888 |
com.app.civilpal.apk |
Android/Spy.AridSpy.A |
AridSpy trojanized utility. |
|
E71F1484B1E3ACB4C8E8 |
prefLog.dex |
Android/Spy.AridSpy.A |
The second stage of AridSpy. |
|
16C8725362D1EBC8443C |
prefLog.dex |
Android/Spy.AridSpy.A |
The second stage of AridSpy. |
|
A64D73C43B41F9A5B938 |
com.rebelvox.rebly.apk |
Android/Spy.AridSpy.A |
AridSpy trojanized utility. |
|
C999ACE5325B7735255D |
replace.apk |
Android/Spy.AridSpy.A |
The primary stage of AridSpy. |
|
78F6669E75352F08A8B0 |
replace.apk |
Android/Spy.AridSpy.A |
The primary stage of AridSpy. |
|
8FF57DC85A7732E4A9D1 |
replace.apk |
Android/Spy.AridSpy.A |
The primary stage of AridSpy. |
Community
|
IP |
Area |
Internet hosting supplier |
First seen |
Particulars |
|
23.106.223[.]54 |
gameservicesplay[.]com |
LeaseWeb USA, Inc. Seattle |
2023‑05‑25 |
C&C server. |
|
23.106.223[.]135 |
crashstoreplayer[.]web site |
LeaseWeb USA, Inc. Seattle |
2023‑08‑19 |
C&C server. |
|
23.254.130[.]97 |
reblychat[.]com |
Hostwinds LLC. |
2023‑05‑01 |
Distribution web site. |
|
35.190.39[.]113 |
proj3-1e67a.firebaseio[.]com proj-95dae.firebaseio[.]com proj-2bedf.firebaseio[.]com proj-54ca0.firebaseio[.]com project44-5ebbd.firebaseio[.]com |
Google LLC |
2024‑02‑15 |
C&C server. |
|
45.87.81[.]169 |
www.palcivilreg[.]com |
Hostinger NOC |
2023‑06‑01 |
Distribution web site. |
|
64.44.102[.]198 |
analyticsandroid[.]com |
Nexeon Applied sciences, Inc. |
2023‑04‑01 |
C&C server. |
|
66.29.141[.]173 |
almoshell[.]web site |
Namecheap, Inc. |
2023‑08‑20 |
Distribution web site. |
|
68.65.121[.]90 |
orientflags[.]com |
Namecheap, Inc. |
2022‑03‑16 |
C&C server. |
|
68.65.121[.]120 |
elsilvercloud[.]com |
Namecheap, Inc. |
2021‑11‑13 |
C&C server. |
|
68.65.122[.]94 |
www.lapizachat[.]com lapizachat[.]com |
Namecheap, Inc. |
2022‑01‑19 |
Distribution web site. |
|
162.0.224[.]52 |
alwaysgoodidea[.]com |
Namecheap, Inc. |
2022‑09‑27 |
C&C server. |
|
198.187.31[.]161 |
nortirchats[.]com |
Namecheap, Inc. |
2022‑09‑23 |
Distribution web site. |
|
199.192.25[.]241 |
ultraversion[.]com |
Namecheap, Inc. |
2021‑10‑12 |
C&C server. |
MITRE ATT&CK methods
This desk was constructed utilizing version 15 of the MITRE ATT&CK framework.
|
Tactic |
ID |
Title |
Description |
|
Preliminary Entry |
Phishing |
AridSpy has been distributed utilizing devoted web sites impersonating professional providers. |
|
|
Persistence |
Boot or Logon Initialization Scripts |
AridSpy receives the BOOT_COMPLETED broadcast intent to activate at gadget startup. |
|
|
Occasion Triggered Execution: Broadcast Receivers |
AridSpy registers to obtain the NEW_OUTGOING_CALL, PHONE_STATE, SMS_RECEIVED, SMS_DELIVER, BOOT_COMPLETED, USER_PRESENT, CONNECTIVITY_CHANGE, ACTION_POWER_CONNECTED, ACTION_POWER_DISCONNECTED, PACKAGE_ADDED, and PACKAGE_CHANGE broadcast intents to activate itself. |
||
|
Protection evasion |
Obtain New Code at Runtime |
AridSpy can obtain first- and second-stage payloads. |
|
|
Obfuscated Information or Info |
AridSpy decrypts a downloaded payload with obfuscated code and strings. |
||
|
Discovery |
Software program Discovery |
AridSpy can determine whether or not Fb Messenger and WhatsApp apps are put in on a tool. |
|
|
Software program Discovery: Safety Software program Discovery |
AridSpy can determine, from a predefined checklist, what safety software program is put in. |
||
|
File and Listing Discovery |
AridSpy can checklist recordsdata and directories on exterior storage. |
||
|
System Info Discovery |
AridSpy can extract details about the gadget together with gadget mannequin, gadget ID, and customary system info. |
||
|
System Community Configuration Discovery |
AridSpy extracts the IMEI quantity. |
||
|
Assortment |
Video Seize |
AridSpy can take images. |
|
|
Archive Collected Knowledge |
AridSpy encrypts information earlier than extraction. |
||
|
Knowledge from Native System |
AridSpy can exfiltrate recordsdata from a tool. |
||
|
Enter Seize: Keylogging |
AridSpy can log all textual content seen and particularly log Fb Messenger and WhatsApp chat communication. |
||
|
Entry Notifications |
AridSpy can gather messages from varied apps. |
||
|
Audio Seize |
AridSpy can file audio from the microphone. |
||
|
Clipboard Knowledge |
AridSpy can get hold of clipboard contents. |
||
|
Location Monitoring |
AridSpy tracks gadget location. |
||
|
Protected Consumer Knowledge: Name Logs |
AridSpy can extract name logs. |
||
|
Protected Consumer Knowledge: Contact Listing |
AridSpy can extract the gadget’s contact checklist. |
||
|
Protected Consumer Knowledge: SMS Messages |
AridSpy can extract SMS messages. |
||
|
Command and Management |
Internet Service: One-Approach Communication |
AridSpy makes use of Google’s Firebase server as a C&C. |
|
|
Exfiltration |
Exfiltration Over C2 Channel |
AridSpy exfiltrates information utilizing HTTPS. |



