iOS and OS X essentially the most weak working programs? Do not confuse vulnerabilities with exploits, or patch frequency with insecurity.
10 Mar 2015
•
,
6 min. learn
Arms up who believes that OS X and iOS are essentially the most weak working programs in use in the present day? Nicely, I discover it a bit onerous to imagine, too, though I’ve had a whole lot of hate-mail through the years for stating that Apple’s working programs will not be invulnerable. But that is the tenor of GFI’s article Most vulnerable operating systems and applications in 2014, primarily based on knowledge from the National Vulnerability Database, and it’s brought about a sure (muted) uproar in safety reporting circles. I believe it’s generated a certain quantity of hate-mail too, judging from the tone of among the feedback to the weblog. Curiously, among the feedback are centred on ‘dangerous journalism’, which appears to overlook the purpose that Cristian Florian is definitely a product supervisor, not a journalist:
‘He at present oversees GFI LanGuard, a profitable community safety scanning and patch administration answer.’
Whereas among the feedback I’ve seen within the safety trade have recommended that this function would possibly make his commentary lower than neutral, I feel it’s honest to imagine that he does know one thing in regards to the matter. However is he proper? Nicely, I suppose it is dependent upon your definition of weak.
Some folks, notably Graham Cluley, have identified some perceived oddities within the methodology behind his conclusions.
…every model of Microsoft Home windows will get its personal entry—however Apple working programs have their completely different variations lumped collectively.
This gave the superficial impression that the article was biased, as a result of in case you added up all of the vulnerabilities for numerous Home windows variations, they got here to 248, much more than the 147, 127 and 119 attributed respectively to OS X, iOS, and the Linux kernel. Florian subsequently took that situation on board and identified that as a result of ‘a whole lot of Home windows vulnerabilities apply to a number of Home windows variations’, the aggregated whole for Home windows could be 68. Nonetheless, it may need been clearer to have break up the opposite working programs by model, too, although his conclusions may need been much less dramatic. The up to date part does profit from a breakdown of vulnerabilities for particular person Linux distributions, nonetheless.
I’ve different issues with the granularity of this commentary, although. The information do inform us one thing in regards to the frequency of updates for particular person platforms, however not how promptly they’re addressed, or whether or not they have been ever exploited and to what extent. Actually, there’s no remediation info in any respect: entries aren’t removed from the NVD database after they’re remediated, and the weblog doesn’t embody info both approach.
Whereas there are pointers right here to particular person vulnerabilities found for every of a number of platforms, however not in regards to the security of the person utilizing the platform: there are various different elements that govern the safety of a system. In spite of everything, each Home windows and Android are topic to a lot increased volumes of malware than both OS X or iOS, although opinion varies on the way to measure the impact of these volumes. And actually, 83% of the vulnerabilities listed are particular to purposes – with a selected emphasis on browsers and different multi-platform utilities (Java, assorted Adobe applications) quite than the working system, which can put the much-hyped struggle of the working programs into perspective.
The up to date article makes it clear that
…the purpose of the article is to not blame anybody – Apple or Linux or Microsoft. The message I’m making an attempt to get throughout is that every one software program merchandise have vulnerabilities.
That appears barely at odds with the unique article and the entire precept of drawing conclusions from a comparability of totals: do we have to know the figures with a purpose to show that ‘all software program merchandise have vulnerabilities? Nicely, maybe we do: it’s clear from some feedback that some commenters are fairly completely happy to disregard the figures in the event that they don’t accord with their anti-Microsoft prejudices.
Florian asserts that the frequency of updates will increase because the product turns into extra standard: that doesn’t appear altogether borne out by the outcomes, given how Microsoft’s market share outweighs that of all different desktop operating systems. Moreover, whereas the distinction between Android and iOS market share is undramatic, the distinction between the six unequivocal vulnerabilities attributed to Android and the 127 apparently loved by iOS customers is. Nevertheless, he doesn’t inform us how most of the 119 Linux kernel vulnerabilities reported apply to Android, and I’m definitely not satisfied sufficient of the worth of this sort of evaluation to go and depend them for myself. I suppose it could possibly be argued that extra effort is put into vulnerability analysis as market share will increase, and fewer as a product matures, however that’s actually speculative.
The corporate sums up:
At GFI we want the folks to make use of the knowledge as a information and to indicate which areas to pay extra consideration to when patching their programs.
That sounds honest sufficient, however until you’re ready to dive into the NVD and CVE websites to take a look at the main points of all these vulnerabilities for your self, I believe that you simply’re not going to be taught way more than that any main working system might have vulnerabilities – as was certainly true again within the heyday of the mainframe – and that sustaining and updating purposes is likely to be as necessary (generally extra so) than sustaining the working system. Although the article does a minimum of observe the NVD’s classification by criticality for every class.
Right here’s why the GFI article worries me, as do (much more) among the extra generalist articles which have picked up uncritically on pretty superficial points of the analysis behind it.
When you’ll excuse a bit private memory… As soon as upon a time my spouse and I owned a small however rambling Victorian villa within the English Midlands. Given its age and its nearness to each a busy railway station and to fluvioglacial landforms, it’s unsurprising that, like many homes within the space of the same age, its exterior partitions had been strengthened in some unspecified time in the future by inserting tie rods. When the time got here for us to go away the realm, we acquired a sure wry amusement from potential consumers who would attempt to beat us down on the worth as a result of they’d observed the anchor plates signifying the presence of tie rods. When you’re considering of shopping for a home in an space like that, would possibly you not truly favor to purchase one the place that reinforcement had already been finished?
In the identical approach, it appears inappropriate to me to encourage the lay reader to measure the safety of an working system by the variety of reported vulnerabilities. Maybe if there’d been extra info than is given on this case in regards to the nature of every vulnerability, hyperlinks or a minimum of appropriate search phrases for trying on the element of the vulnerabilities, and data on how responsive the businesses behind the software program have been in every case, the article would have been extra helpful. I admire, in fact, that such a degree of element would have required appreciable effort, however I’m positive it could have been appreciated by the ‘IT directors’ who have been addressed right here.
In case you are in search of Home windows-specific info on vulnerabilities and patching at a a lot larger degree of element, I’m inclined to advocate this report from one in all my colleagues at ESET: Windows Exploitation in 2014.
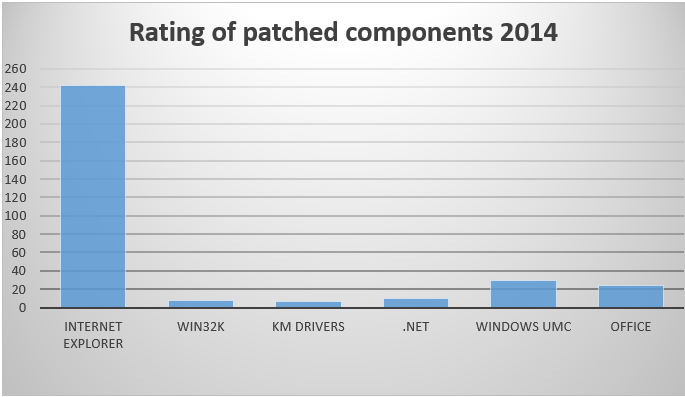
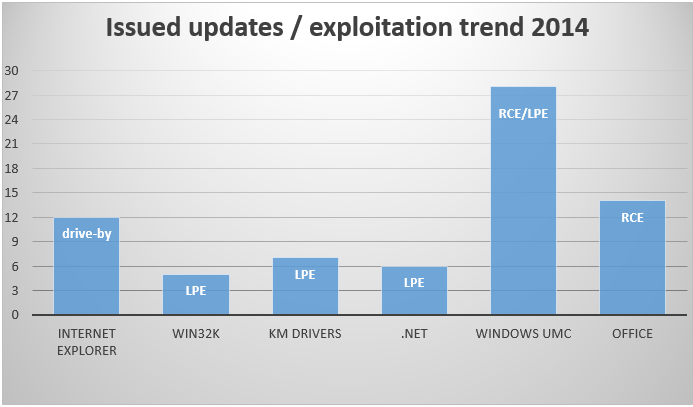
It’s significantly centered on Web Explorer – unsurprisingly, given what number of patches it wanted in 2014 in comparison with different Home windows elements – however can be informative on the distribution of particular varieties of exploit.
This determine from the 16-page paper reveals distribution relative to drive-by, LPE (Native Privilege Escalation) and RCE (Distant Code Execution) exploits throughout a variety of elements, together with Kernel Mode (KM) drivers and Consumer Mode Parts (UMC).