Scams
What are a number of the commonest giveaway indicators that the particular person behind the display or on the opposite finish of the road isn’t who they declare to be?
18 Apr 2024
•
,
5 min. learn

Our world is turning into extra impersonal because it turns into extra digital-centric. And since we are able to’t see the particular person or group on the different finish of an electronic mail, social media message or textual content, it’s simpler for scammers to fake to be one thing or somebody they’re not. That is impersonation fraud, and it’s quick turning into one of many highest earners for cybercriminals. According to the FTC, scammers impersonating companies and governments made $1.1 billion from their victims in 2023.
Impersonation fraud can take many types, however along with your eyes on the tell-tale indicators of a rip-off, your private info and hard-earned cash will stay below lock and key.
What does impersonation fraud appear to be?
Like most fraud, impersonation scams are designed to get you to ship the dangerous guys cash, or private/monetary particulars which they will both promote on the darkish net or use themselves to commit id fraud. Phishing is probably the obvious taste of impersonation fraud: a scammer contacting you pretending to be a trusted entity requesting cash or info.
However there are different varieties. Faux social media accounts are a rising problem; used to unfold rip-off hyperlinks and too-good-to-be-true presents. And faux cell apps would possibly impersonate respectable apps to reap private data, flood your display with advertisements or enroll you in premium-rate providers.
Impersonation scams are additionally evolving. In response to the FTC, they more and more blur channels and methods, in order that “a pretend Amazon worker would possibly switch you to a pretend financial institution or perhaps a pretend FBI or FTC worker for pretend assist.”
The right way to spot the scammers
Opposite to widespread perception, it’s not simply the aged who’re in danger from impersonation scams. Research in the UK discovered that individuals below 35 usually tend to have been focused by and fallen for one of these fraud. With that in thoughts, look out for these warning indicators:
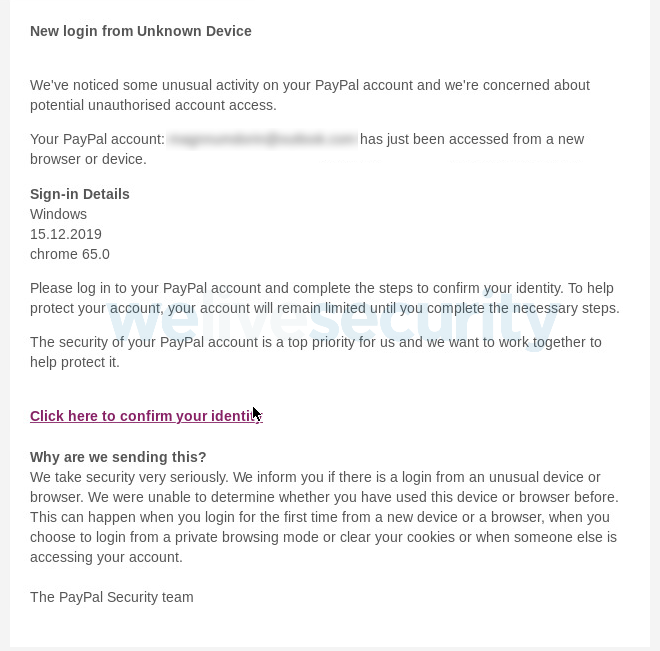
- Requests for cash: A message on electronic mail, textual content or DM from somebody purporting to be an in depth member of the family or contact. They’ll request pressing monetary help as a consequence of some excuse resembling they’re stranded abroad or wanted medical assist. Fraudsters can hijack respectable social media and electronic mail accounts to make it appear as if it’s actually your good friend/member of the family contacting you.
- Distant entry: In tech assist fraud, an official from a tech firm, telco or different legitimate-seeming group requires entry to your pc for some made-up purpose resembling it’s compromised with malware.
- Entry to your account: A police officer or authorities official contacts you out of the blue claiming cash in your account must be analyzed as a part of an investigation into cash laundering, drug smuggling or another critical crime. They provide to ‘maintain it protected’ by transferring it elsewhere.
- Stress: The particular person on the opposite finish of the cellphone, electronic mail, textual content or social media channel pressures you to behave instantly. They’ll attempt to panic you into making a choice with out pondering – resembling sending cash to a good friend in peril, or transferring urgently to a authorities official. It’s a traditional social engineering approach – typically even performed in particular person or with a probably scary twist courtesy of AI instruments that may be co-opted to perpetrate digital kidnapping scams.
- Faux couriers retrieving cash: An official presents to ship a courier to come back to your property handle to choose up money, playing cards, useful gadgets or PINs below all kinds of pretend pretexts, resembling serving to your relative get out of bother or to resolve a dodgy cost in your financial institution card.
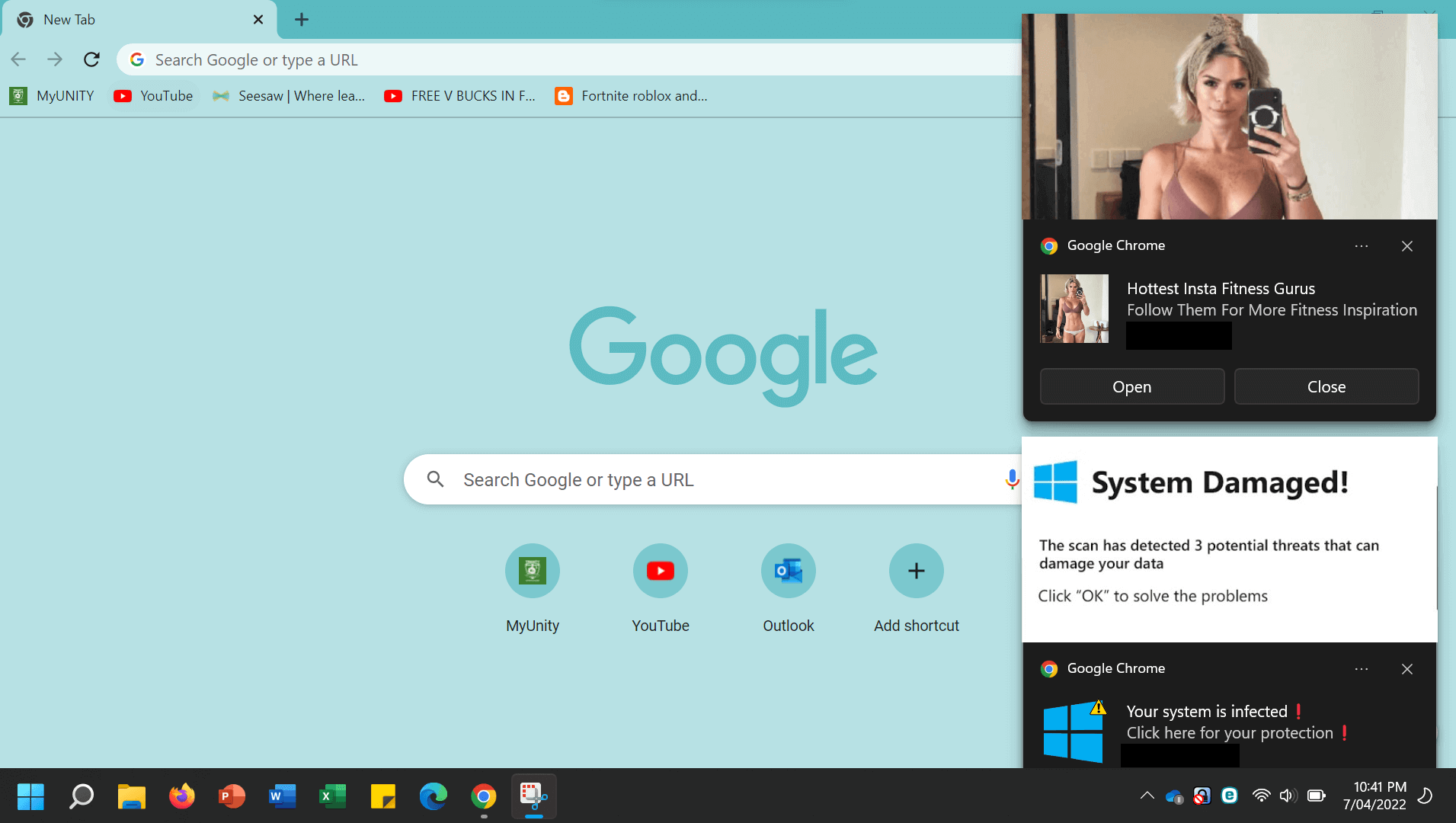
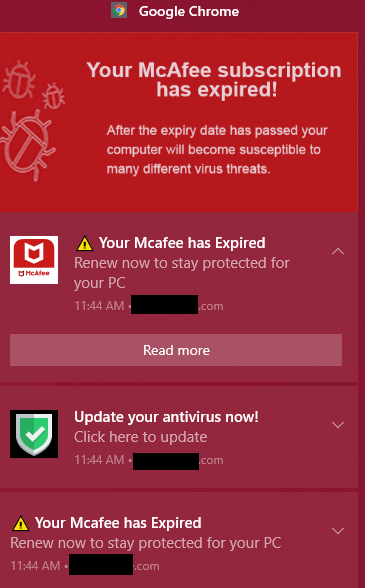
- Account safety alerts: These pretend notifications usually require you to ‘verify’ your particulars first – one other method for scammers to pay money for your private and monetary info.
- Uncommon messages: Phishing emails usually include inconsistencies which mark them out as impersonation fraud. Scammers will attempt to spoof the show title to impersonate the sender. However by hovering over the title, you’ll be able to see the masked electronic mail handle beneath, which can be an unofficial-looking one. Remember, nevertheless, that scammers also can hijack respectable electronic mail accounts and use caller ID spoofing to make it more durable to inform the true from the pretend.
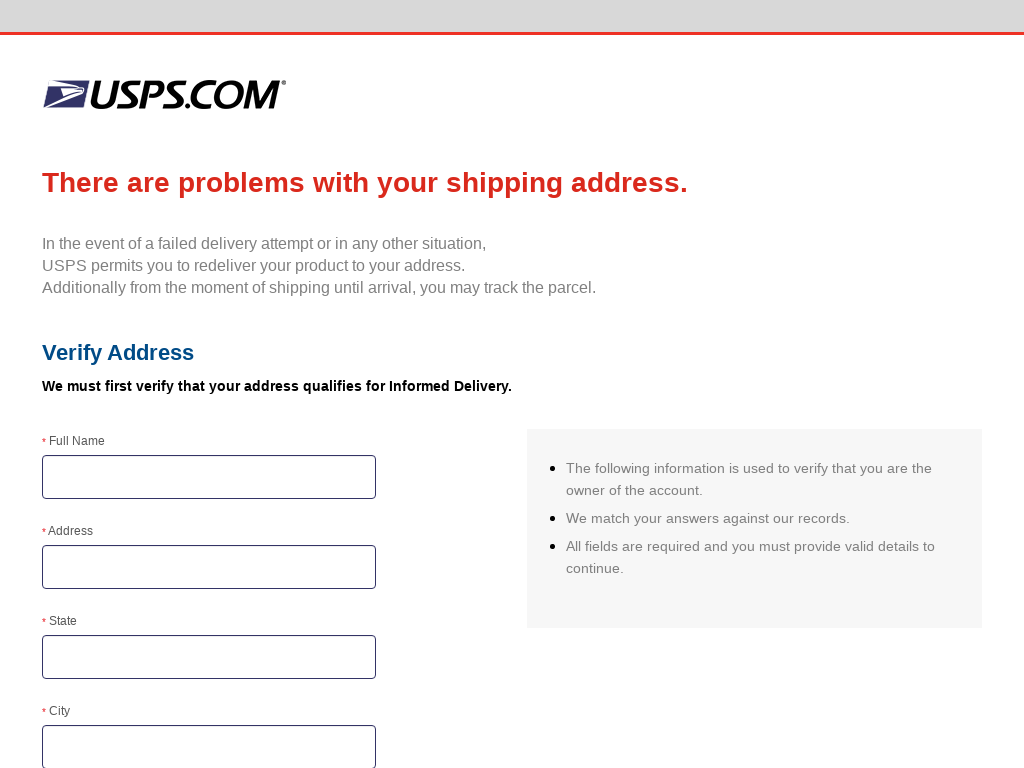
- Faux supply points: Legit-looking postal/logistics companies demand that you just pay a small charge or hand over financial institution particulars to allow protected supply of your non-existent parcel. In different situations, fraudsters will pose as a well known supply service and warn you of ‘issues’ along with your package deal.
- Reward playing cards: You’re requested to pay fines or one-off charges by shopping for high-value gadgets or reward playing cards. The scammer needs you to do that slightly than a financial institution switch, because it’s far harder to hint.
- Faux subscription renewals: These might require you to attach the scammer to your pc to resume your subscription or course of a non-existent refund.
- Fictitious giveaways or reductions: These require you to pay a small ‘charge’ in an effort to declare them. For sure, there isn’t any reward or low cost as that is merely a variation on the advance charge fraud.
- Uncommon language: One other tell-tale signal of phishing makes an attempt may very well be poor grammar and spelling or imprecise language in messages – though with fraudsters utilizing generative AI to create their pretend messages, that is turning into much less frequent.
Keep alert
Keep in mind, impersonation scams are always evolving, so the above is definitely not an exhaustive checklist. The subsequent evolution in such scams is coming because of AI-powered deepfakes, which might mimic the voice and even look of a trusted particular person. These are already tricking workplace employees into making big-money corporate fund transfers to accounts below the management of cybercriminals. And the know-how is getting used to impersonate trusted individuals on social media in an effort to trick followers into making rash investments. As deepfakes develop into cheaper and extra accessible, they may be utilized in smaller scale fraud.
With any impersonation fraud, the secret is: be skeptical, decelerate, and independently confirm they’re who they are saying they’re. Do that by reaching out to the group or particular person immediately, don’t reply to an electronic mail or cellphone quantity listed on the preliminary message. And by no means hand over cash or private info except you’ve confirmed the contact is respectable.




